Does an article posted by The American Report prove China and Russia hacked the 2020 Election and does it show IP addresses from China, Russia, Hong Kong, Germany, Canada and the Czech Republic hacking "PA, NV, MI, GA Battleground States"? No, that's not true: the article appears to rely on data screenshotted from an anonymously registered website launched on December 15, 2020, that on closer inspection appears to be a poorly-made forgery.
The American Report published an article (now offline but archived here) on January 11, 2020, under the title "EXCLUSIVE: Proof China, Russia Hacked 2020 Election: IP Addresses In China, Russia, Hong Kong, Germany, Canada, Czech Republic Hacked PA, NV, MI, GA Battleground States Raw Data Analytics Show". It opened:
Raw data analytics exclusively obtained by The American Report show that during the 2020 presidential election internet protocol (IP) addresses in China, Russia, Hong Kong, Germany, Canada, and the Czech Republic hacked into IP addresses in the battleground states of Pennsylvania, Nevada, Michigan and Georgia.
It backs up this assertion with the following screenshot, which it claimed could be found on "blxware.org" and by clicking on "Scorecard" on that site. If you do that you are taken to "electionrecords.com," a site that was registered anonymously on December 15, 2020 and that appears to be collecting donations on behalf of "Dennis Montgomery" via crowdfunding site GivSendGo (archived here) "to expose the truth about Hammer and Scorecard" (a conspiracy theory that we have written about here that The American Report also publicized heavily). Montgomery appears to have a history of pushing this story and other conspiracies in the past (see AZCentral and The Daily Beast).
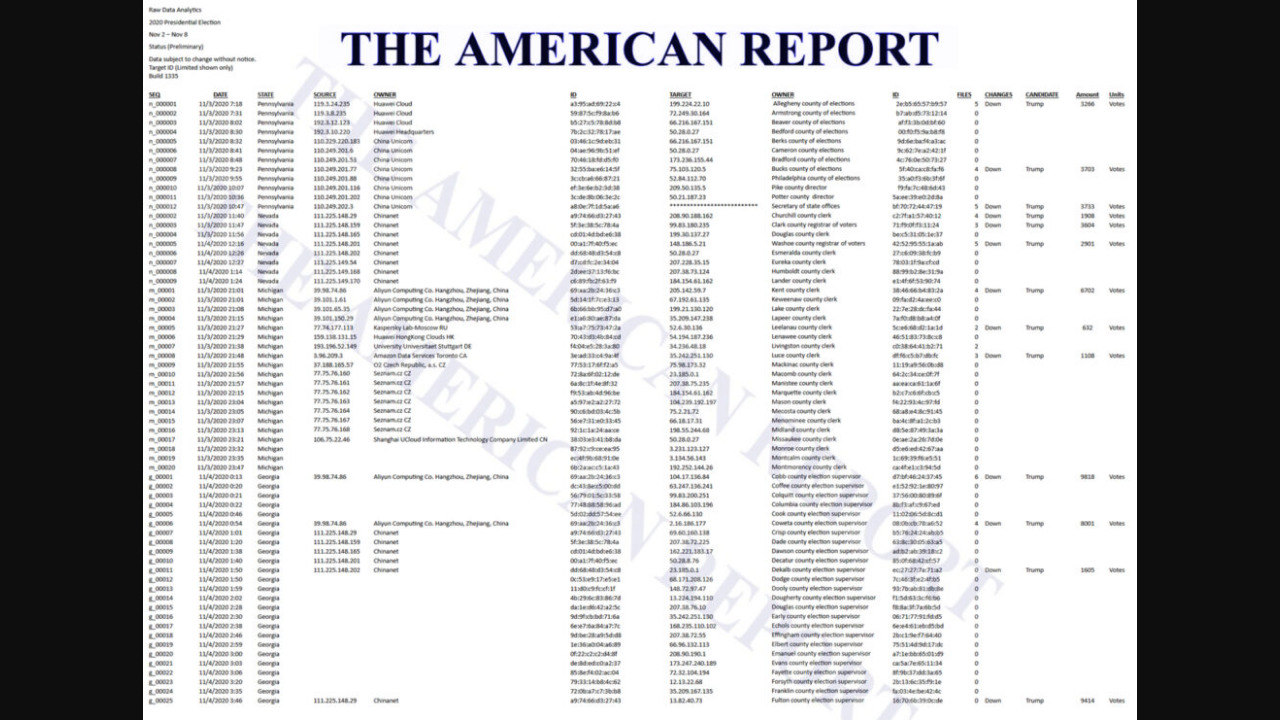
(Source: image captured from The American Report by The Internet Archive, archived here)
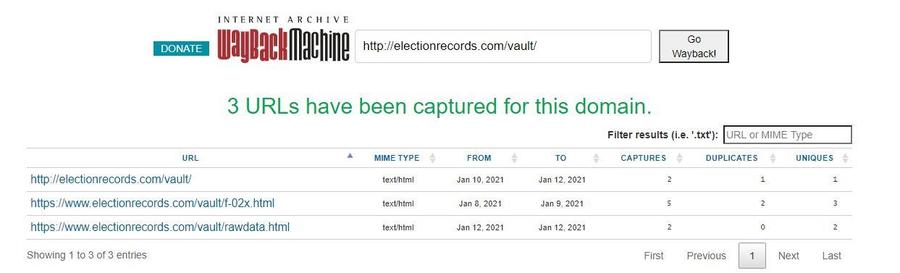
The "electionrecords.com" site contained a link labeled "Data analysis in progress 01/04/21 16:21 PST" which pointed to https://www.electionrecords.com/vault/f-02x.html which currently returns a 404 error.
A snapshot of that page can still be found on the Internet Archive, however, and it appears it contains the top part of the list shown in the screenshot: https://web.archive.org/web/20210108162018/https://www.electionrecords.com/vault/f-02x.html
Some further digging on the Internet Archive brought up one more file in that "vault" folder: https://web.archive.org/web/*/http://electionrecords.com/vault/*
And indeed, the "rawdata.html" file appears to contain the same data from the screenshot, with some minor differences: https://web.archive.org/web/20210112040134/https://www.electionrecords.com/vault/rawdata.html
The "Election Records" website offers no detailed explanation of what this data is or where it came from, other than a vague notice on the front page of the site:
Data was collected by current and previous US GOV contractors and reported on by our journalists voting data in over 3,000 county and regional election offices before, during, and after Nov 3, 2020, just as we did in 2008, 2012, and 2016 and have the raw data to support the vote totals listed here and will make the data public when the analytical work is completed.
Data is being processed on various cloud networks, keeping it out of the reach of those that want to suppress, steal, or destroy the data as they have done in the past so many times.
amg
Lead Stories reached out to the email address listed on the site to ask about the source of the data and the method by which it was created and will update this story when we receive a reply.
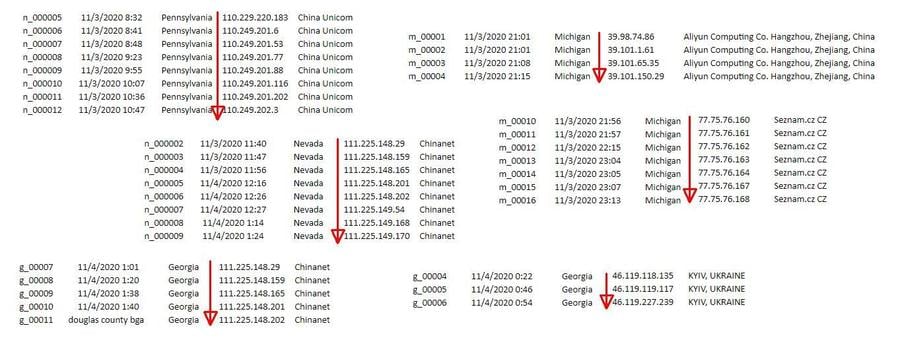
The data has columns labeled "SOURCE" and "TARGET" which supposedly show which IP address was "hacked" by which other one at a time and date mentioned in a "DATE" column but it does not explain how this happened or how it was determined. Most of the "source" IPs have additional columns linking them to various foreign companies or institutions while the "target" IPs are all labeled as being owned by various counties in Pennsylvania, Nevada, Michigan and Georgia. Additional columns appear to show the number of files that were "hacked" along with the number of votes that were supposedly changed along with the direction of the change and the name of the candidate. Unsurprisingly all the changes are marked "Down" and they all affect "Trump". For some reason the majority of the "hacks" in the list do not appear to have vote change columns associated with them.
(None of these vote changes were detected during the three manual recounts in Georgia by the way, so to lend these allegations credibility one has to assume these "hacks" also managed to change the ink-on-paper ballots stored in several county warehouses).
Lead Stories checked some of the IP addresses in the "target" column and they do indeed all seem to belong to various county websites, so whoever created this list did their homework on that part. There are, however, several glaring anomalies in the data that point to this being a crude forgery that was manually created and not the output of a computer program/analysis:
1. Neatly sorted IP ranges
The "DATE" column seems to imply all this data is chronological, i.e. it shows the "hacks" in the order they happened in time.
But several of the "foreign" IP addresses in the "SOURCE" column appear neatly sorted, as if they were plucked from the internet from lists of IP addresses that belong to certain corporations or groups. What are the odds hackers would neatly time their attacks so their originating IP addresses are nicely sorted?
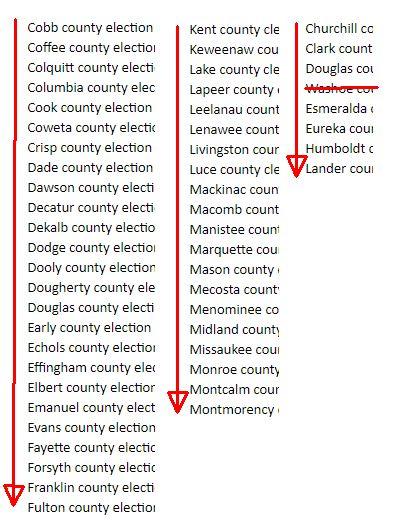
2. Alphabetically sorted county names
Even if the hackers did their attacks from a list of target IPs and they indeed went top to bottom, there are other oddly tidy lists. For instance, they attack the county websites in perfect alphabetical order too, timed perfectly from different ranges of IP addresses in different countries? What are the odds?
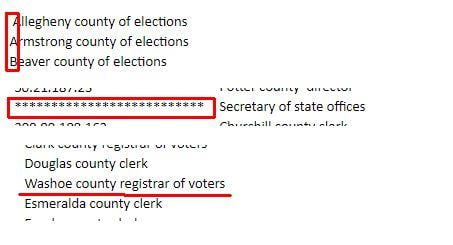
3. Manually changed entries
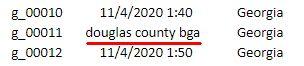
And if we grant the theory of hackers working down a list of IP addresses and working down an alphabetical list of counties, then why do some items appear out of whack, almost like they were entered by hand? "Allegheny" is out of alignment, the "Secretary of state offices" entry doesn't have an IP address and "Washoe county" is strangely out of alphabetical order. And one of the entries in the "DATE" column reads "douglas county bga" for some reason.
4. County of elections, director, clerk, registrar & election supervisor entries all neatly grouped
One final oddity: the names of the entities that supposedly "own" the IP addresses display a weird pattern.
- The first ones are almost all "X county of elections"
- Then we have two "X county director" entries
- Next follows the (only) "Sectretary of state offices"
- Then we have four lines alternating between "X county clerk" and "X county registrar of votes"
- Followed by a slew of "X county clerk" entries
- And once we are in Georgia every IP is owned by the "X county election supervisor".
Those anomalies don't seem to cluster by state:
- Pennsylvania has a mix of "county of elections," "director" and "Secretary of state offices"
- Nevada has a mix of "clerk" and "registrar of votes"
- Michigan only has "clerk"
- Georgia only has "election supervisor"

Note that most county websites are used for more than just the election, they usually also carry information about police, schools, roads, health care, etc. So it would be weird for the website to be registered by the "registrar of votes," the "county of elections" or the "election supervisor" as well.
But what are the odds the hackers would attack from perfectly sorted IP addresses, alphabetically by county and then group their attacks by the type of entity that owns the IP address? All the while leaving no trace in the paper ballots used in manual recounts and audits?
And the only site that has this data doesn't disclose its methods and it is associated with a known peddler of conspiracy theories?
Given all the above we are confident in labeling the data above as nothing more than a crude forgery for now, as no credible evidence is presented anywhere on the site that would explain these anomalies (or even the sourcing and method used to generate the data).