
Summary: Mike Lindell's video series allegedly proving fraud in the November 2020 elections relies heavily on digital evidence in the form of files and animations that Lindell claims show attacks on the U.S. election infrastructure coming from China and other places. Lindell has never acknowledged where these files and animations came from. Lead Stories traced them back to a website apparently run by Dennis L. Montgomery, a man with a long history of being closely connected to cases involving fraudulently manufactured evidence. We are making these files available in this article so anyone can examine them for themselves.
Mike Lindell has promised on the air to go over this article line by line. We sincerely hope you do, Mike, and we are especially interested in your reaction to the questions at the very end. We are concerned you may have been taken for a ride by people who just want to take advantage of your passion for election security in order to use you for their own gain.
The January 9, 2021 Evidence
In the wake of the November 4, 2020, presidential election results showing a Joe Biden win over Donald Trump, MyPillow CEO Mike Lindell has been trying to convince the public the election was stolen through fraudulent means. He has promoted a variety of theories on how this was accomplished (and who did it) and presented those theories in three online videos he co-produced (click the titles to read what we wrote about "Absolute Proof," "Scientific Proof" and "Absolute Interference"). Claims that Dominion voting machines were somehow involved led to Dominion filing a $1.3 billion lawsuit against Lindell and his company MyPillow Inc. Lindell responded with a $1.6 billon lawsuit of his own against Dominion.
During an interview on the "Jimmy Kimmel Live!" show on April 28, 2021, Lindell repeatedly said he only got the most important evidence on January 9:
At 5:25 in the interview he says:
I didn't get anything until January 9th, and this was something different. This was the machines, this was an attack through the machines, you've seen it.
At 6:23 Kimmel challenges Lindell to show the evidence he is supposedly going to take to the Supreme Court:
You have said repeatedly you are bringing this evidence. I assume you haven't seen this evidence. Have you seen it? (Lindell: 'Oh, yes, I've seen it.') Why is it taking so long if this is such a serious thing?
Lindell replies:
As you've seen in 'Absolute Interference,' the new one I've put out, there's a cyber ... It's a white hat hacker that works for the government, one of the best in the world. When our country is attacked these are the guys that go in, for the cyberattacks, and check it all out and validate it. So I hired them to validate the evidence that I have these guys brought me over here. Now realize Jimmy, the only reason I have the evidence is I became a voice after January 9th, where they are going: 'Hey, we've tried to get this out there,' and nobody had.
Time-stamped lists and animations
So which evidence is he talking about here?
In the "Absolute Interference" video Lindell interviews an anonymous person he claims is an expert in cybersecurity who he hired to validate the data file and animations originally presented in "Absolute Proof" on February 5, 2021. They were presented by a "Mary Fanning," who, according to Dominon's lawsuit (page 35) might be a retired homemaker named Mary Kirchhoefer who has several published articles on various conservative-leaning websites, according to her Muck Rack profile.
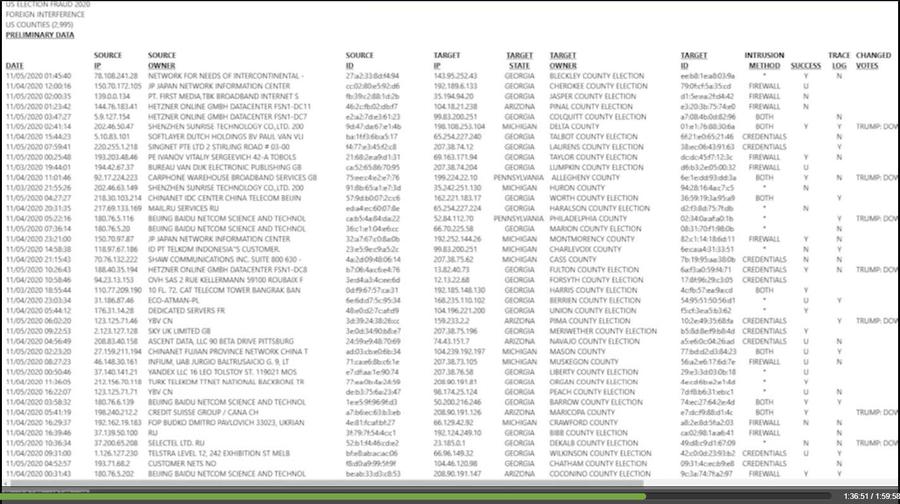
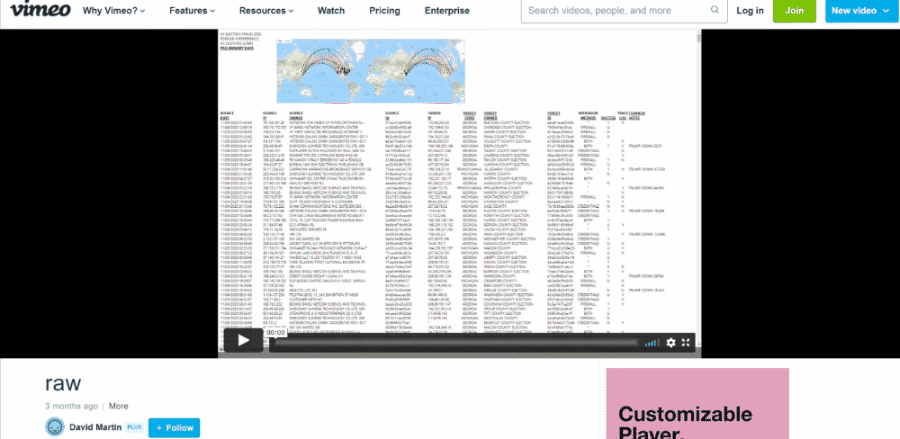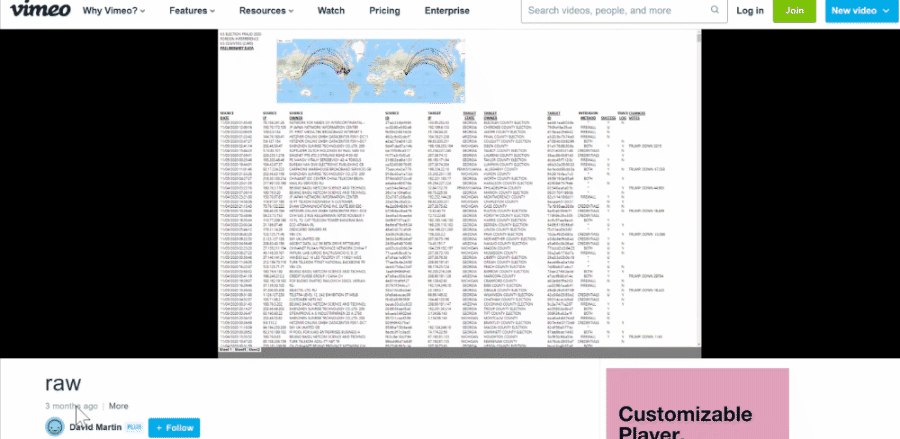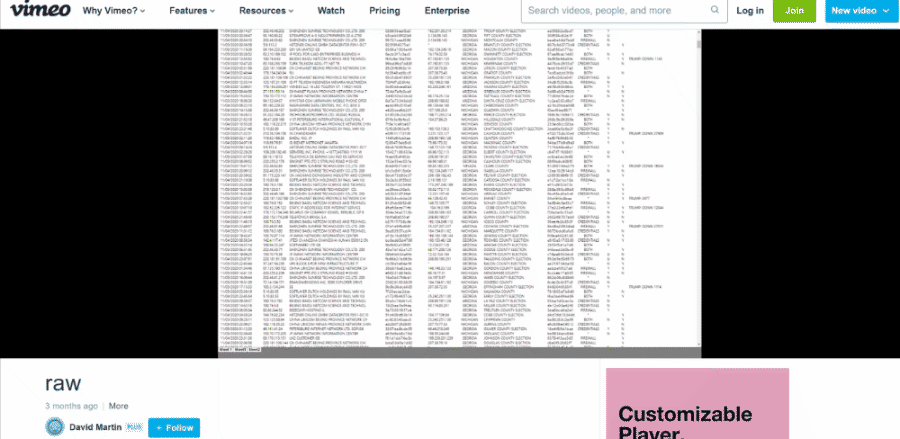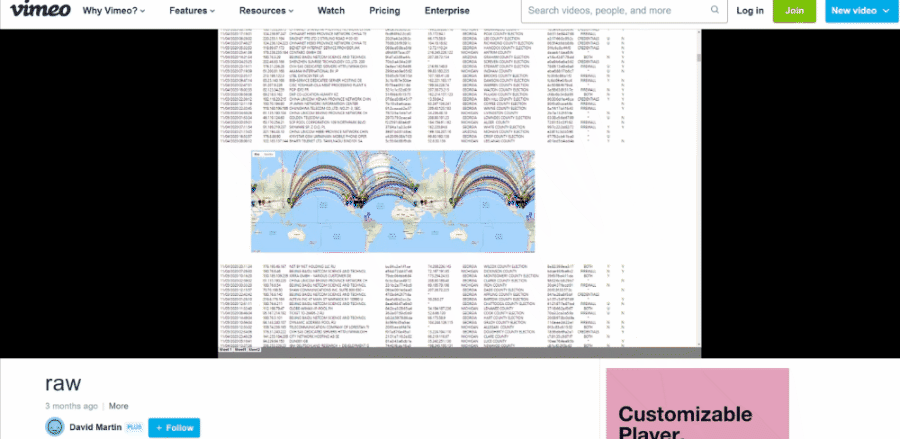
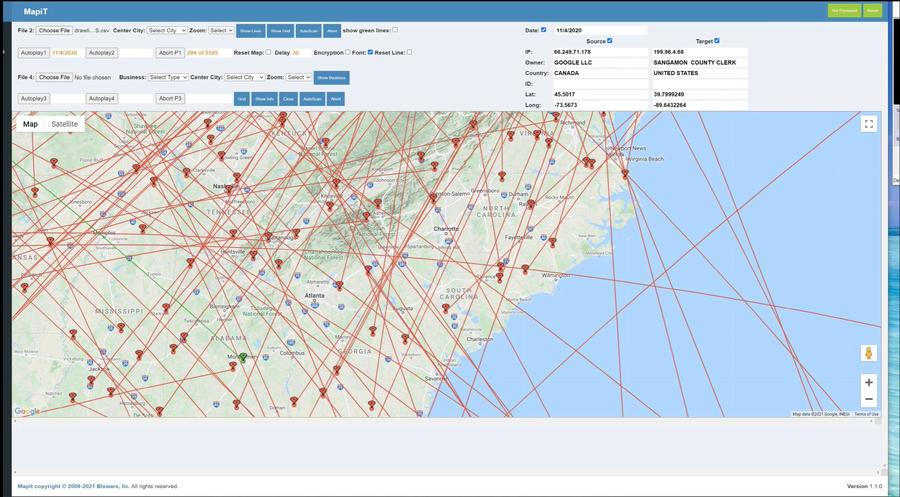
This is what the data looked like in Lindell's video:
(Source: screenshot taken by Lead Stories of "Absolute Proof" at 1:36:51)
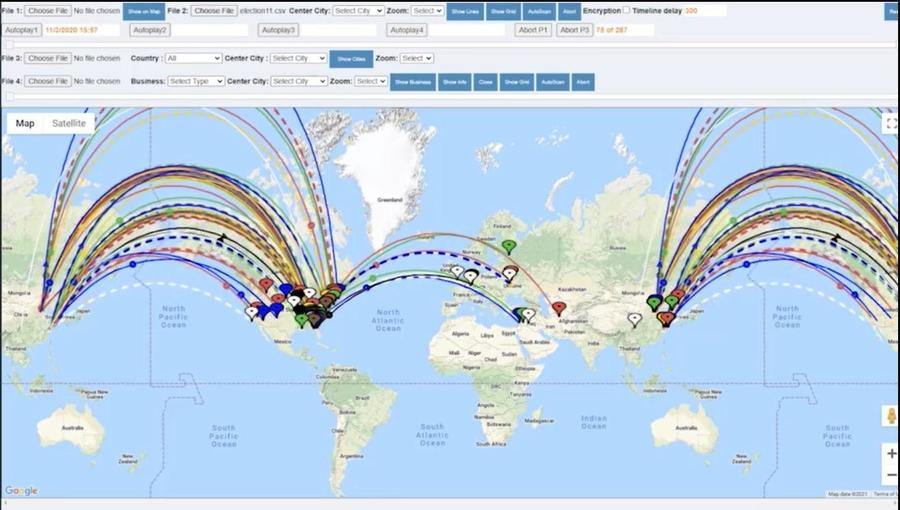
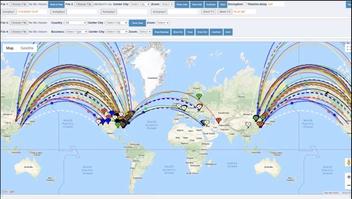
She also presents an animation of what she claims is a recording of how the attacks went down in real time:
(Source: screenshot take by Lead Stories of "Absolute Proof" at 1:44:44)
In the "Absolute Interference" video (at around 1:41:30) Mike Lindell calls this evidence "a cyber-footprint that is locked in time" and something that "can't be changed in any way, shape or form."
In that case, we are sure he will love what The Wayback Machine does. It describes itself as:
... an initiative of the Internet Archive, a 501(c)(3) non-profit, building a digital library of Internet sites and other cultural artifacts in digital form.
In essence it is a site where you can go back in time and see what a website (or a page on a website) looked like on a particular day and time. The site works by automatically taking a huge number of snapshots of sites and pages. It is used by researchers, fact-checkers, cybersecurity analysts and journalists who want to investigate things that were deleted or changed on the internet.
To give a few quick examples of what it can do: You can see what President Donald Trump's Twitter account looked like just before it got banned in 2021 or go all the way back to his first tweets in 2009. Similarly, it has 187 snapshots of the main page of Lindell's Twitter account taken over a period of several years. Or you can see what the website of mypillow.com looked like in 2011 if you want to take a trip down memory lane. You can even check out the old 2015 look of Lead Stories before our redesign.
In the article below we will make extensive use of The Wayback Machine to unearth now-deleted pages and to point out ways in which articles have been changed over time. Whenever you see a link followed by "(archived here)" the word "here" links to a copy of the article stored at the Internet Archive's Wayback Machine so you can still read it even if it no longer exists at the original site.
Fanning to Lindell via Howse
So it seems pretty clear that the time-stamped lists and animations were the evidence Lindell was talking about to Kimmel. But how did those get from Fanning to Lindell?
The answer to that question can be found in this January 18, 2021 article on WorldViewWeekend by Leo Hohman (archived here):
Jones and Fanning saw their website, TheAmericanReport.com, attacked by outside hackers after they published a report detailing information from former government sources that recorded in real time how the election was stolen.
The details included in their report include the IP addresses and the owner of the IP addresses which hacked into the Nov. 3 election.
....
Fanning called Howse on Saturday, Jan. 9, and asked if he knew of any other possible sources of communicating the information to Trump.
Howse could only think of one man. Mike Lindell, who had been on his radio show in the past and Howse had kept his phone number on file.
"I said 'let's call him.' So we called and spent the next 20 minutes or so briefing him until he understood it fully," Howse said on Monday, Jan. 18. "There are many external hard drives full of this documentation."
Notes:
- Jones is Alan Jones, Fanning's frequent co-author on the website The American Report.
- Howse is Brannon Howse, host of "Worldview Weekend," an online broadcaster. The studio set for Worldview Weekend is also where Lindell's three movies would later be produced:
(Source: screenshot taken by Lead Stories of "Absolute Proof")
The same set is now also used to do the broadcasts on Lindell's Frank Speech network:
(Source: screenshot taken by Lead Stories of Frank Speech livestream)
So Howse put Lindell in touch with Fanning and Jones, but where did they get the files and animations?
From Dennis L. Montgomery to Mary Fanning & Alan Jones
Jones and Fanning are listed as the authors on several articles on a website named The American Report. On October 31, 2020, they published an article that claimed a secret supercomputer named "The Hammer" running a software application named "Scorecard" would be used by Biden to steal votes during the election, according to information they say they received from "CIA contractor-turned-whistleblower Dennis Montgomery." Lead Stories wrote about those false claims here. The central idea to the claim was that the votes were being stolen "at the transfer points of state election computer systems and outside third party election data vaults as votes are being transferred," using a "prismatic scoring algorithm" supposedly created by this Dennis Montgomery.
As Lead Stories pointed out at the time, one of these "transfer points" mentioned in the American Report article was run by a company that didn't even handle vote tabulation (they only handled voter check-in in some places, which does not involve ballots or counting votes). The article also failed to point out what these "outside third party election data vaults" supposedly were, since official election data is normally kept by the Secretaries of State and not by outsiders. And according to Google the term "prismatic scoring algorithm" was never used prior to October 31, 2020 when it first appeared in the Fanning and Jones article without further explanation.
Since 2017 Fanning and Jones published dozens of articles (archived here) on their website about Montgomery or relying on him as a source, frequently describing him as "former NSA/CIA contractor-turned whistleblower Dennis Montgomery" or similar terms.
On November 12, 2020, they claimed (archived here) Montgomery told them the election was stolen by the Democrats using "cloned, identically-sized blocks of Biden votes" through "multiple injections" in "10 states."
On November 28, 2020, Fanning appeared by phone in a broadcast on "Worldview Weekend" together with retired Gen. Thomas McInerney, making false claims that special forces had seized servers in Frankfurt, Germany that were connected via Spain to several U.S. states, and making several other false claims related to the election. The U.S. military has denied such an operation took place. McInerney would later also appear in Lindell's movies.
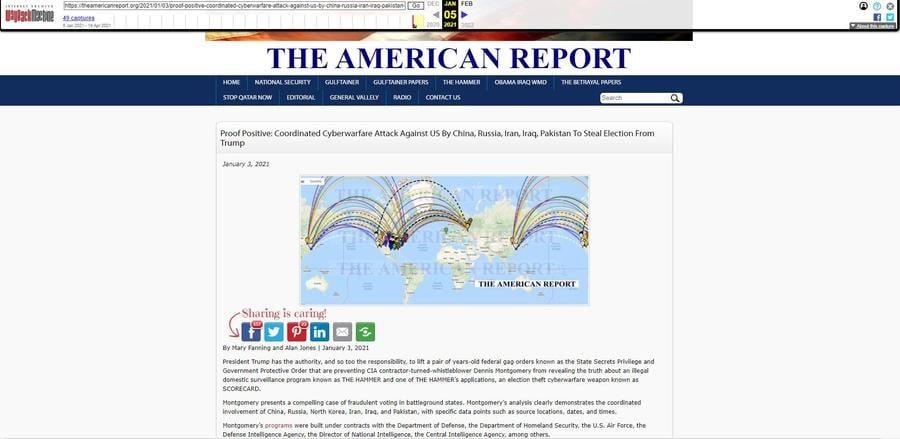
On January 3, 2021, Fanning and Jones first published something very similar to what was shown in the Lindell movie in an article titled "Proof Positive: Coordinated Cyberwarfare Attack Against US By China, Russia, Iran, Iraq, Pakistan To Steal Election From Trump" (archived here). That article featured a graphic very similar to the animations later shown in "Absolute Proof." The article also linked to a site named "blxware.org" and said it contained "programs" from Dennis Montgomery. Later in the article there is also a link to "https://www.blxware.org/scorecard/index.html" where it claims video can be seen of the "cyberwarfare attack."
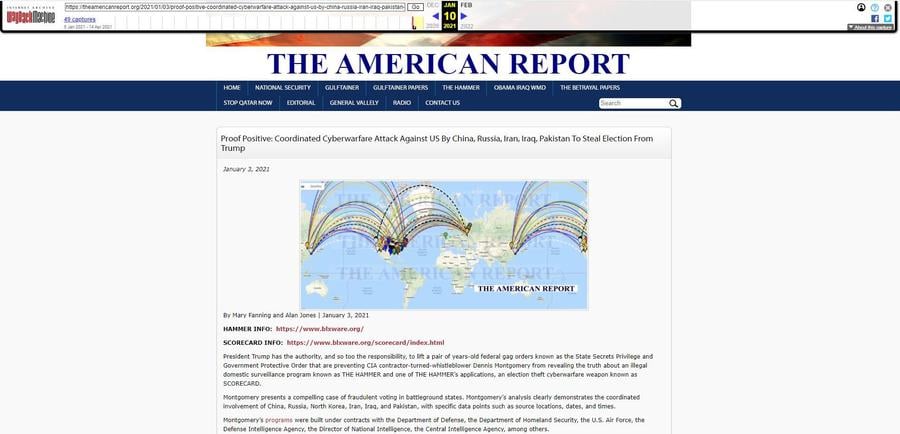
By January 10, 2021 those links were made much more prominent by adding them to the top of the article as "HAMMER INFO" and "SCORECARD INFO." It is unclear when this happened exactly but it was definitely after January 6, 2021 as that was the last time The Wayback Machine stored a version that did not have that change:
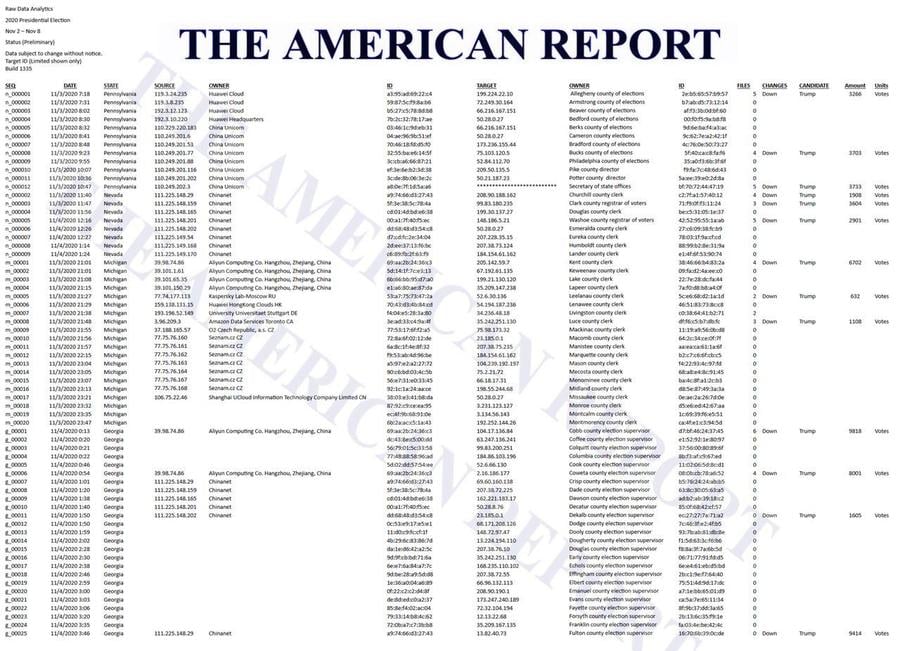
On January 11, 2021, The American Report published another article (archived here), this one titled "EXCLUSIVE: Proof China, Russia Hacked 2020 Election: IP Addresses In China, Russia, Hong Kong, Germany, Canada, Czech Republic Hacked PA, NV, MI, GA Battleground States Raw Data Analytics Show," which contained a graphic that purports to show a list of time-stamped attacks against U.S. election targets originating from Chinese IP addresses.
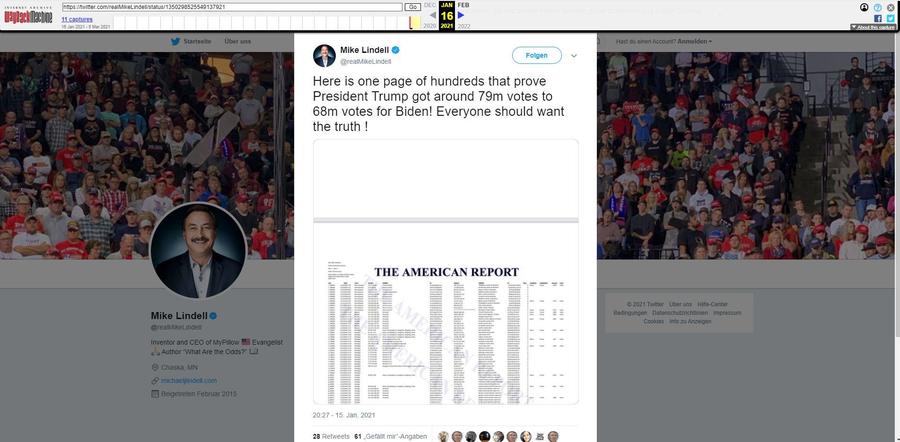
Note that this graphic was not used in "Absolute Proof" but Mike Lindell did use it in a tweet on January 15, 2021 (archived here):
On January 18, 2021, Lead Stories did an analysis of the data from the screenshot and concluded it was fraudulent because among other things it contained several mistakes that pointed to the file being created by hand. To quote from that fact check:
It backs up this assertion with the following screenshot, which it claimed could be found on "blxware.org" and by clicking on "Scorecard" on that site. If you do that you are taken to "electionrecords.com," a site that was registered anonymously on December 15, 2020 and that appears to be collecting donations on behalf of "Dennis Montgomery" via crowdfunding site GiveSendGo (archived here) "to expose the truth about Hammer and Scorecard" (a conspiracy theory that we have written about here that The American Report also publicized heavily).
and
The "electionrecords.com" site contained a link labeled "Data analysis in progress 01/04/21 16:21 PST" which pointed to https://www.electionrecords.com/vault/f-02x.html which currently returns a 404 error.
A snapshot of that page can still be found on the Internet Archive, however, and it appears it contains the top part of the list shown in the screenshot: https://web.archive.org/web/20210108162018/https://www.electionrecords.com/vault/f-02x.html
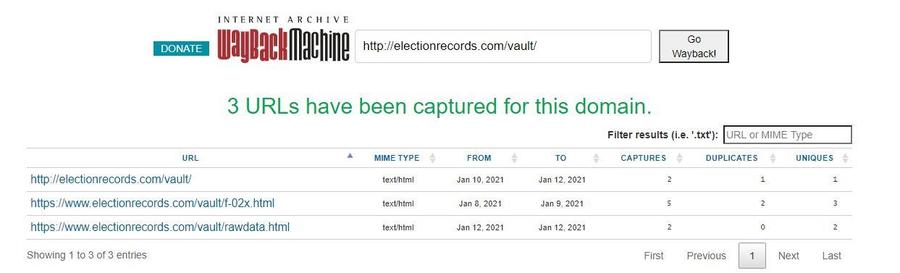
Some further digging on the Internet Archive brought up one more file in that "vault" folder: https://web.archive.org/web/*/http://electionrecords.com/vault/*
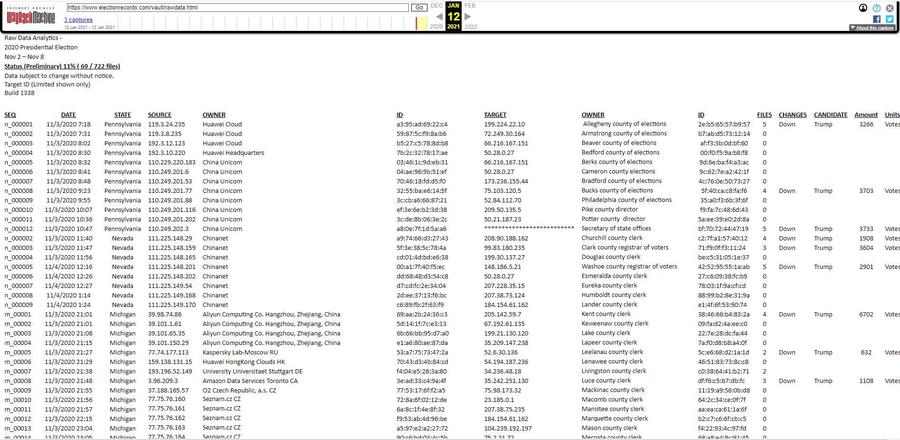
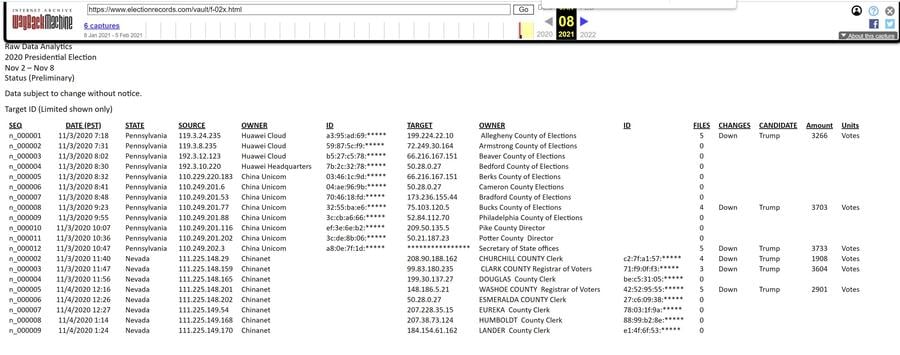
And indeed, the "rawdata.html" file appears to contain the same data from the screenshot, with some minor differences: https://web.archive.org/web/20210112040134/https://www.electionrecords.com/vault/rawdata.html
More files on electionrecords.com
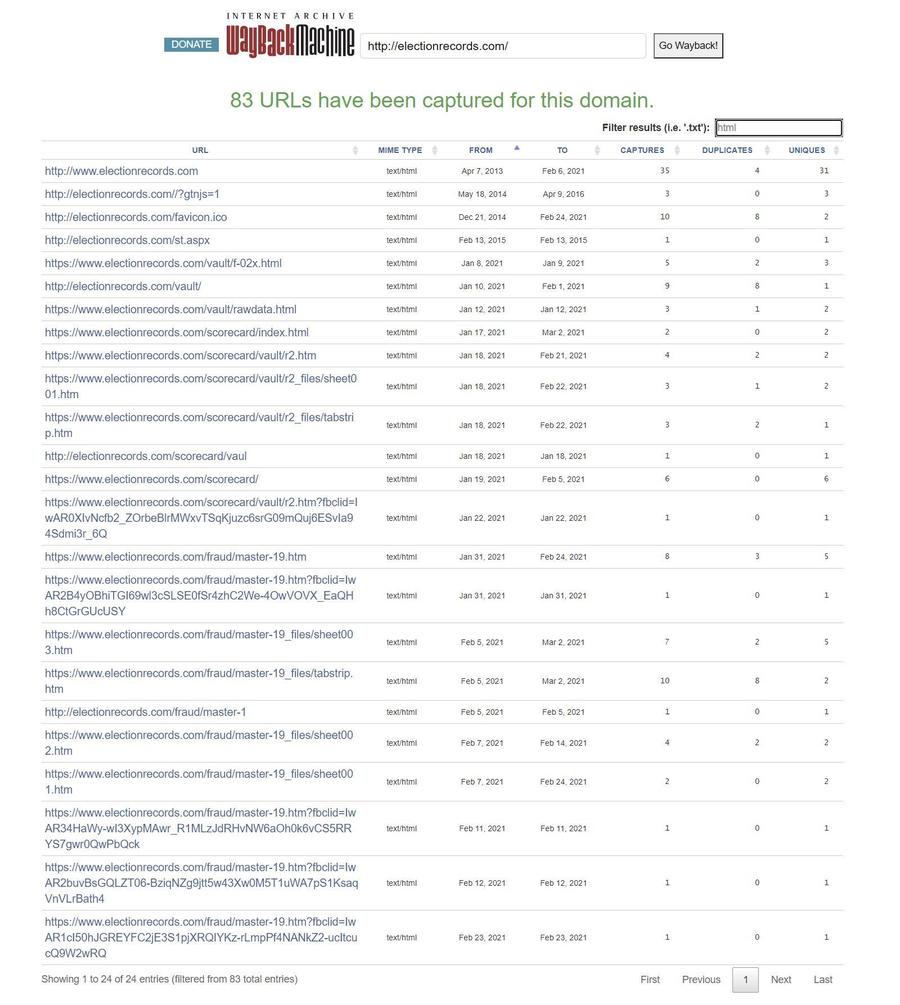
Using The Internet Archive's Wayback Machine, Lead Stories was able to uncover several other pages that used to exist on the "electionrecords.com" website:
Note that the site appeared to have been briefly active in 2013 but that it was then inactive for several years. The Internet Archive capture in 2016 indicated the domain was for sale so it only effectively came back to life in early 2021 or perhaps late 2020.
Besides the "rawdata.html" file there are three more interesting files there: "f-02x.html," "r2.html" and finally "master-19.html." If you put them in order it seems f-02x.html was a trial run made on or just before January 8, 2021, consisting of just a handful of lines and with several columns still lacking data for multiple rows:
Followed by rawdata around January 12, 2021 or a few days before that (this is the file of the screenshot used by Fanning in the January 11, 2021 article and Lindell in the January 15, 2021 tweet) where more lines have been added.
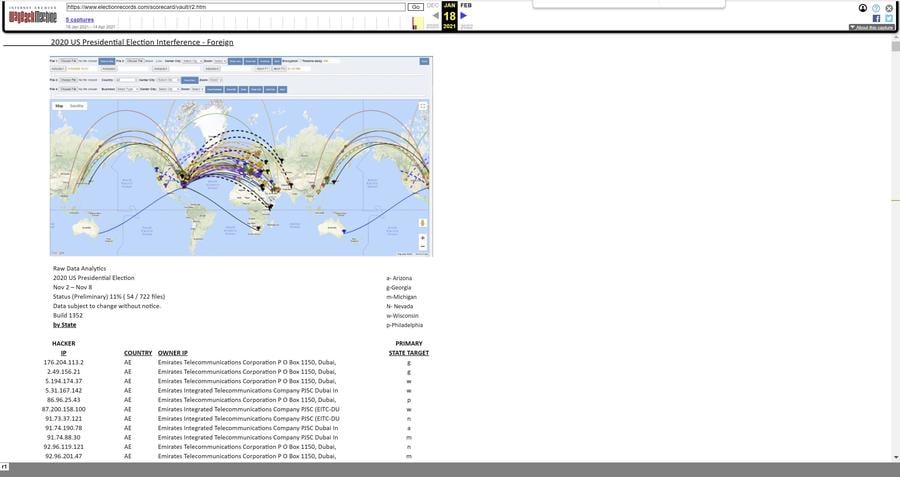
Then on January 18, 2021 (or slightly before that) we see the r2.html file, which is much longer and has the typical map again, but now with totally different colums: Targets are now identified only by a single letter indicating the state and there is way less information about the supposed type of attack.
On January 31, 2021, the Internet Archive first records the "master-19.html" file, which has about 2,400 lines of data with multiple columns, exactly the same data that was seen in the screenshot/animation in "Absolute Proof" at the top of this article:
That file had three tabs at the bottom labeled "Sheet 1," "Sheet1" and "Sheet2" and an earlier file had a tab labeled "r1." These tabs might be a telltale sign that the files were created by saving an Excel sheet (which can have similar tabs) in the HTML file format (a type of file optimized for viewing as part of a website).
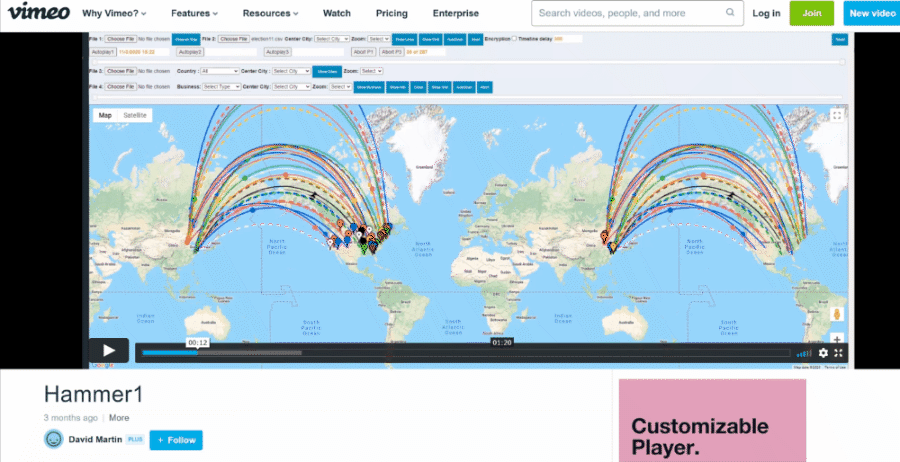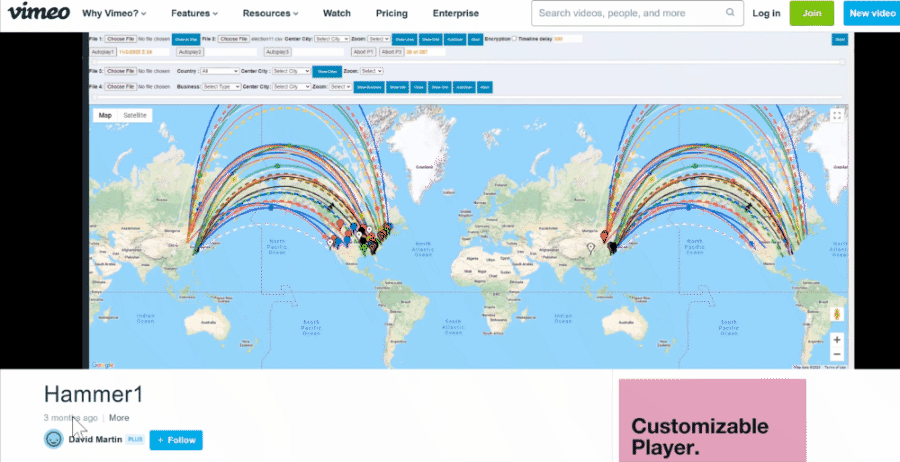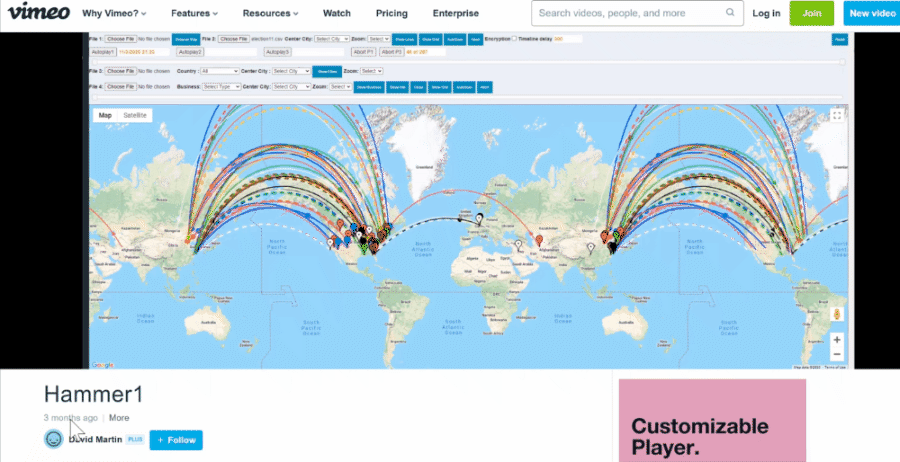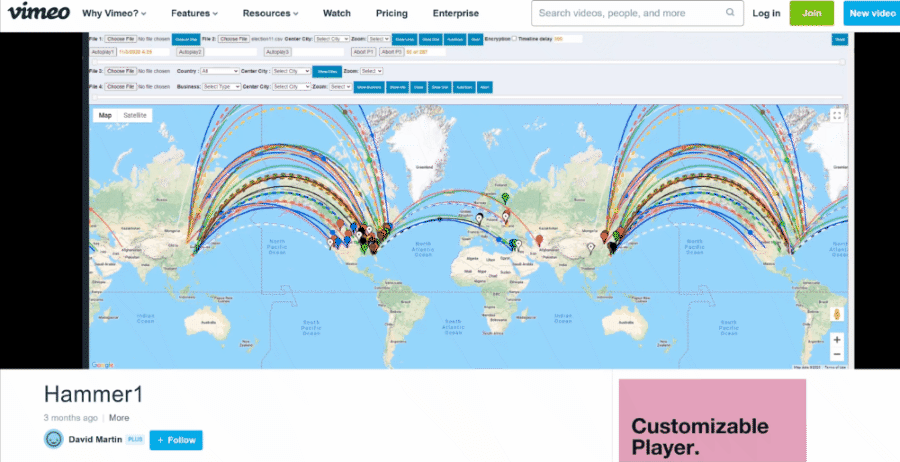
It also contains two links labeled "DATE - PLAY VIDEO" and "ATTACK - PLAY VIDEO," which lead to two videos hosted on Vimeo named "raw" and "Hammer1," both uploaded by an account named "David Martin" on January 29, 2021. These match the types of videos also seen in the Mike Lindell's movies. We have made animated gifs of what the videos looked like because they might get deleted later:
Patrick Byrne also involved somehow?
The very same "raw" video is also embedded in a January 31, 2021 article on the blog of Patrick Byrne (CEO of overstock.com) titled "How DJT Lost the White House, Chapter 2: Was there Foreign Interference in this Election? You Make the Call." (archived here). In the original version captured by The Wayback Machine, he writes this:
I shall start with an analysis of the packet traffic on Election Day 2020. As packets travel through the Internet they leave a trail, and dolphin-speakers using the right tools can, in a sense, 'shine a light' and reveal those packet trails in the cyber-fog. Here is a video of only 1 minute which shows hundreds of foreign entities (many in China) who, on November 3, 2020, were hitting voting machines across Pennsylvania, Michigan, Wisconsin, Arizona, Nevada, and Georgia.
What are "dolphin speakers," you might ask? According to the Wayback Machine, by February 2, 2021 Byrne's original article was updated with some extra info and a download link added to now read like this:
In this chapter I will follow that principle. I start with an analysis of the packet traffic on Election Day 2020 provided me by the best cyber-forensics specialist (aka 'dolphin-speaker') I have ever met. As packets travel through the Internet they leave a trail, and dolphin-speakers using the right tools can, in a sense, 'shine a light' and reveal those packet trails in the cyber-fog. The cyber-specialists to whom I refer, who has access to such tools (and even more arcane ones), has documented vote-flipping in the Problematic 6 states amounting to 299,567 votes, just enough in each state to flip the election. 43% of that activity came from China.
For people who wish to study the Excel sheet behind this data, click here. US Election Fraud 2020_General For those who shudder at the thought of opening an Excel spreadsheet, this 1 minute video shows hundreds of foreign entities (many in China) who, on November 3, 2020, were conducting Man-in-the-Middle attacks on election system across these states of Pennsylvania, Michigan, Wisconsin, Arizona, Nevada, and Georgia in order to flip votes.
(Boldface highlighting added by Lead Stories)
So a "dolphin-speaker" is just a fancy word for a computer forensics expert in Byrne's lingo.
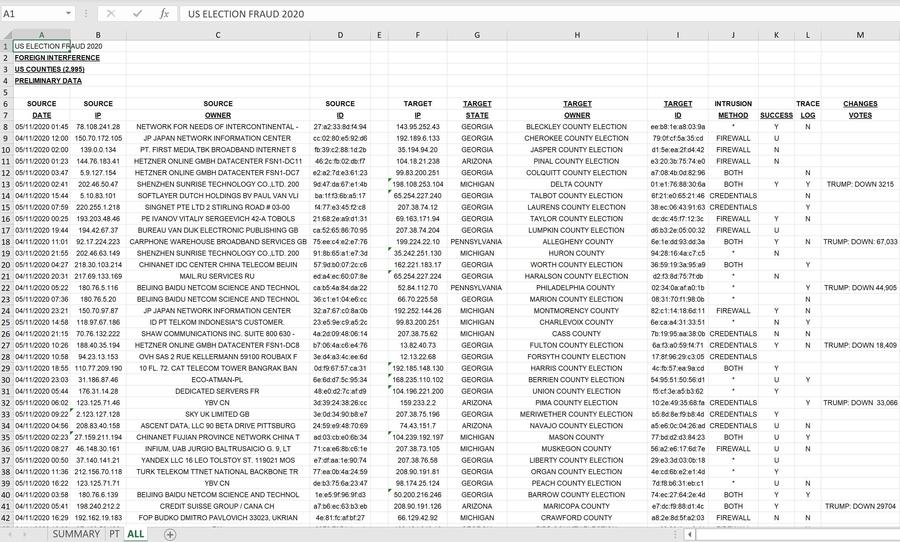
The "Excel sheet behind this data" posted on Byrne's site can still be downloaded from the Internet Archive. It looks like this, and if that looks familiar it is, because it is the exact same data that can be found the "master-19.html" file shown in the "Absolute Proof" video:
The metadata in the Excel file indicates it was created on January 31, 2021 by "Microsoft Office User" but last edited on February 2, 2021 by a user named "patri":
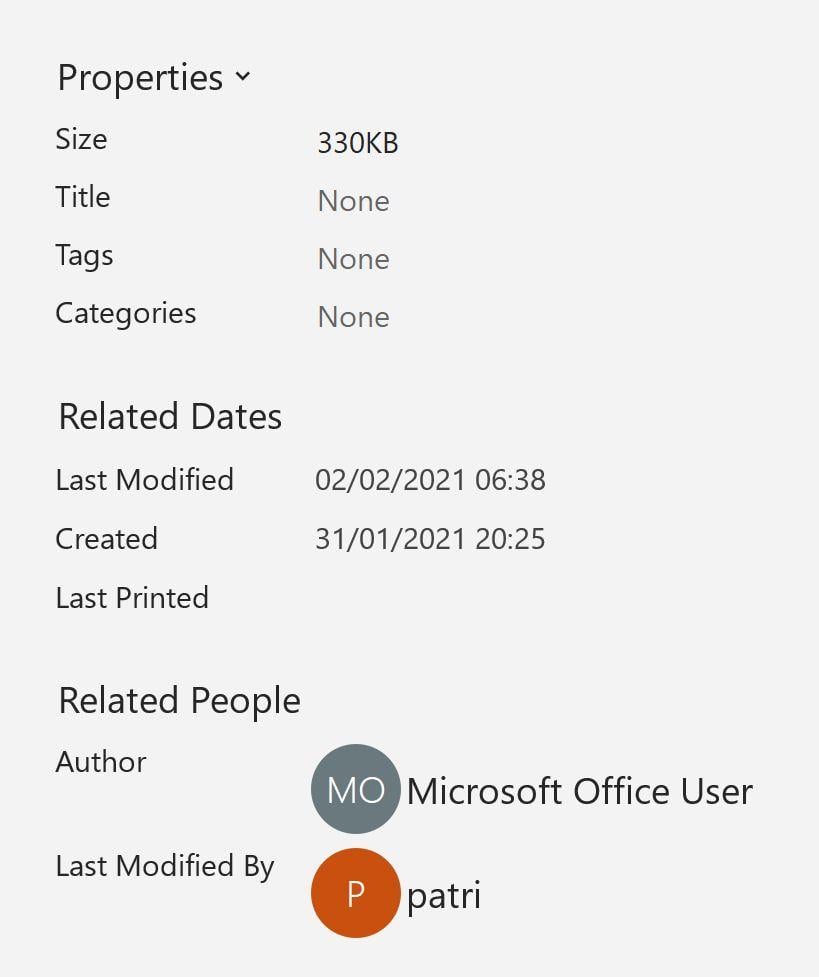
Of course, this is not proof Patrick Byrne created the file. If he even is the actual "patri" user it could be that he just slightly edited the layout before uploading the file to his website. And we don't know if he is the "Microsoft Office User" who created the file. We have reached out via the email address listed on Byrne's website to inquire about the origin of the file and will update this story when we receive a reply.
It is interesting to see it appears to have been created on January 31, 2021, the exact same day the master-19.html file first appeared on the Internet Archive. But the animation showing data from the master-19.html file was already uploaded by the "David Martin" account on Vimeo in January 29, 2021 so we know the dataset definitely existed before that.
Interestingly enough, the "David Martin" account on Vimeo remains active to this day. On April 29, 2021 it uploaded a new video named "wave4.mp4" (archived here):
In the bottom left corner you can see a copyright message that reads "MapIt copyright © 2009-2021 Blxware, llc" while at the top the application appears to be named "MapiT."
Blxware & Dennis Montgomery
So what is Blxware and this blxware.org site? According to one of the earliest Internet Archive captures of the site in September 2020:
This site is created and maintained by former Blxware employees that wanted the truth about Blware owner, Edra Blixseth, her US GOV contracts, and Blxware's work in illegal FBI/CIA/NSA domestic surveillance programs to be exposed to the public.
As we've shown earlier, the Blxware.org site was registered anonymously but it had a link that sent people to electionrecords.com, which collected donations on behalf of Dennis L. Montgomery. Fanning and Jones also made several references to Blxware.org being the site of Montgomery.
According to his LinkedIn profile, Dennis L. Montgomery was indeed the CTO of a company named "BLXWARE". You can read Montgomery's story in this Seattle Weekly article by Rick Anderson in 2014, including the probable reason why he soured on "BLXware":
Montgomery ... discovered a new benefactor, Edra Blixseth, wife of billionaire developer Tim Blixseth. The couple ... ended up backing him along with investor and former presidential candidate Jack Kemp.
Montgomery formed a new company he ultimately called BLXware. That provided him with the kind of money you need to drive a $70,000 Porsche Cayenne GTS and, in one day at a California casino, lose $422,000.
The Blixseths moved to Medina in 2007 and divorced in 2008, and Edra filed for bankruptcy in 2009. Onetime billionaire Tim has since filed too, and last month was trying to head off the sale of his $8 million Medina home.
AZCentral reported in 2015 about a lawsuit involving Sheriff Joe Arpaio who had paid Montgomery a large sum of money to collect evidence for him, evidence that court documents said ultimately turned out to be bogus:
Arpaio acknowledged his agency's relationship with Montgomery in bombshell testimony this April, during a hearing designed to address separate contempt-of-court allegations stemming from the racial-profiling suit. Arpaio readily admitted that Montgomery's information was "junk."
Another AZCentral story from 2020 cited from an internal email from the Sheriff's office:
One internal email stated: 'After reviewing all the hard drivers our experts concluded that Dennis Montgomery deliberately compiled massive amounts of data on to these drives for the purpose of obfuscating the fact the data itself contained no evidence to support Dennis Montgomery's claims.'
That's not the only story about Montgomery. Writing about him in 2009, Wired said this:
A programmer who claims he produced software that detected hidden terrorist messages in Al Jazeera broadcasts was apparently responsible for a false alert in 2003 that grounded international flights.
And
His company got a contract with the Air Force to handle video shot by unmanned Predator drones. He claimed his program could recognize weapons in the surveillance video. In 2004 the U.S. Special Operations Command reportedly gave his company a $30 million no-bid contract for 'compression' and 'automatic target recognition' technology. Montgomery even got a security clearance. But a former worker told Playboy that he had helped fake some 40 demonstrations of the software.
In January, 2006 Montgomery left the company over disputes with one of his business partners and investors. The company claims the software disappeared and the source code was wiped out when Montgomery left. Hard drives that supposedly stored backup copies of the programs turned out to contain nothing. Montgomery has been called a 'habitual liar engaged in fraud' by one of his former attorneys and was charged in Las Vegas with bouncing nine checks in the amount of $1 million in September 2008. He was arrested on a felony warrant in California.
IEEE Spectrum, the magazine of the Institute of Electrical and Electronics Engineers, wrote in 2010:
Self-proclaimed 'scientist' Dennis Montgomery convinced the Bush White House, the CIA, and the Air Force that he could predict terrorist attacks. Specifically, he asserted that the Al Jazeera TV network was transmitting data to Al Qaeda sleepers, consisting of 'latitudes and longitudes and flight numbers.' Hundreds of canceled flights and holiday disruptions later, it turned out that the government contracts were based on faked demonstrations. Because his technology did not actually work, Montgomery was staging rigged demonstrations, faking the results of his 'special' image processing algorithm by having someone hide behind a wall and press a button, reminiscent of the Great and Terrible Oz.
Now, when somebody with a reputation like Montgomery's claims to have documented proof of election tampering we wouldn't blame you if you were a little skeptical at first. There is, of course, always the possibility that maybe *this* time he got it right and he obtained actual data from unimpeachable sources, but we would totally understand it if you wanted to see every detail, source and method first.
And what if you can literally see him create the timestamp files over a period of several days via the Internet Archive Wayback Machine?
Would we bet the future of our company, Lead Stories, and our employees on that, sight unseen?
Being professional fact-checkers, you can bet we'd have some questions first.
Rounding up the claims
As the graphics and lists appeared in several places, claims about what exactly they were actually showing have also shifted considerably over time.
- Initially Fanning and Jones claimed The Hammer was a surveillance tool originally developed by Montgomery for use against America's adversaries, but later used to illegally spy on President Trump and others.
- The October 31, 2020, article from Fanning and Jones emphatically claimed it was "Biden" stealing the election with Hammer and Scorecard, in eight states, namely "Florida, Georgia, Texas, Pennsylvania, Wisconsin, Michigan, Nevada, and Arizona" (several of which Trump actually won). And that it was done "by tampering with the computers at the transfer points of state election computer systems and outside third party election data vaults as votes are being transferred" (i.e. not via voting machines). The way in which it was accomplished was supposedly "a prismatic scoring algorithm that Montgomery created."
- The November 12, 2020, article they wrote says it was "Dems" according to Montgomery, and that it was done by using "cloned, identically-sized blocks of Biden votes" through "multiple injections" in "10 states."
- Their January 3, 2021, story claims it was done by "China, Russia, North Korea, Iran, Iraq, and Pakistan" because suddenly there are now also HAMMERs in the U.K. and China somehow.
- In the "Absolute Proof" video, Fanning claims at 1 hour, 38 minutes, 30 seconds that "intrusions" were accomplished using "fake credentials" because there were "false administrators placed on the Secretary of State's computers" or alternatively by "breaking through the firewall" (and sometimes both) to "steal" votes and that "over 60% of these intrusions come from China, so, that is, over 66% is what the number is."
- In the January 31, 2021, story, Patrick Byrne claims (based on the same data) only 43% of the activity came from China. And he claims they were using "Man-in-the-Middle attacks" to "flip" votes.
- In the third video in the series, "Absolute Interference," the focus is almost exclusively on proving the attacks came from China.
So, what does the data show? Is it a system in China or in several other countries? Is it "flipping" votes, "stealing" or "injecting" them? In eight states or in 10 states? Via "man-in-the-middle" attacks or through "tampering with computers at transfer points"? Or was it by using "fake credentials" or "breaching the firewall"? And were they attacking "third party election data vaults" or the "Secretary of State computers"? And what is a "prismatic scoring algorithm" anyway?
Or was it a bit of everything? And if so, why can't they keep their story straight?
Or is all of this just a collection of random cybersecurity buzzwords that will easily impress people who do not know that "IP" in "IP address" stands for Internet Protocol?
Questions for Mike Lindell
Before publication of this article we reached out to Mike Lindell by email and asked him if, to his knowledge, he directly got any of his data from Dennis L. Montgomery, Patrick Bryrne, David Martin, blxware.org or electionrecords.com. He told us by email he didn't and said he only recognized two names in the list. He claimed "my information is unique and involves other sources. Whistleblowers and white hat hackers employed by the government and the private sector."
All of the above raises several questions for Lindell. But before we get to that, I want to make one thing clear because Lindell and his co-hosts on Frank Speech seem to be very sensitive on this point:
None of the above is in any way, shape or form a Lead Stories endorsement, defense or praise for China, the Chinese Communist Party, communism or the Soviet Union. Communist regimes in general have terrible records when it comes to democracy, press freedom and human rights. They have falsified history, imprisoned fact-checkers and shot journalists. We endorse none of that. Our co-founder Alan Duke volunteered to join the U.S. Army, which at that time was fighting Communists in Vietnam. Duke was only prevented from joining that fight because the war ended before he could complete his military training.
We agree there definitely is real historical evidence of China or Communists doing terrible things. However the data discussed in this article is not it.
With that out of the way:
- If, after all that, you still believe our fact check is ideologically motivated, how do you explain The Gateway Pundit coming to the same conclusion (archived here and here) using the very same expert they used to verify the Hunter Biden laptop? Or these people on the forum of Steve Bannon's podcast?
- How much vetting was really done on Fanning and Jones?
- Is any vetting of Montgomery in the cards? If not, why not?
- If the data came from unnamed "whistleblowers and white hat hackers" that were not in the list Lead Stories asked you about, does that mean Fanning and Jones were wrong when they repeatedly wrote it came from Montgomery?
- Why do you think Fanning did not mention Montgomery in your movies, but can't seem to stop writing about him on her own site?
- When discussing our article about "Absolute Interference" during the livestream on frankspeech.com you and Douglas Frank swatted aside our question of how all the hacking and vote stealing/flipping/injecting could also alter the paper ballots that were recounted several times (including by hand) in two states, by saying "it's more complicated than that." We are still waiting for that very complicated answer.
- Do you think there are people who have a financial or other interest in keeping you in the dark about the real nature of these time-stamped files and animations?