STORY UPDATED: check for updates below.
Did a set of computer backups released at Mike Lindell's Cyber Symposium prove Dominion Voting Systems erased "election logs" from Mesa County, Colorado, voting machines after the 2020 election? No, that's not true: Independent cybersecurity experts at the event said the two backup copies (called "images") turned out to be from two different servers and cannot logically be used to make a before-and-after comparison to prove data had been wiped off a voting machine.
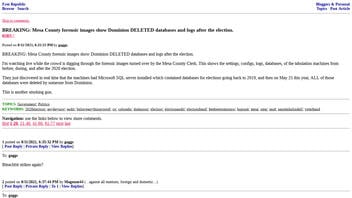
The claim was made several places on social media including an August 11, 2011, FreeRepublic.com blog post (archived here) titled "BREAKING: Mesa County forensic images show Dominion DELETED databases and logs after the election." which opened:
They just discovered in real time that the machines had Microsoft SQL server installed which contained databases for elections going back to 2019, and then on May 25 this year, ALL of those databases were deleted by someone from Dominion.
This is another smoking gun.
BREAKING: Mesa County forensic images show Dominion DELETED databases and logs after the election.
Dominion Voting Systems spokesperson Kay Stimson wrote in an August 13, 2021, email to Lead Stories that the company will not comment on the Cyber Symposium because it has an active defamation lawsuit against Lindell.
To ensure accuracy and provide independent expert context for our assessment of evidentiary computer files Lindell promised to release, Lead Stories arranged to send to the symposium Robert Graham, a cybersecurity expert well known for inventing several internet security tools.
When the two system image files were circulated, Graham was in one of the two breakout rooms where two dozen IT and cybersecurity experts gathered. They were waiting for Lindell to release "packet capture" data Lindell says is proof the 2020 election was hacked. Lindell never released that material.
On the second day of the symposium, Lindell's team released a new set of computer system backup copies -- sometimes called server images -- offered as proof that Dominion Voting Systems had suspiciously cleaned out the memory and settings of a Mesa County, Colorado, voting machine.
Graham said the copies of the server images were said to have been downloaded from a public site using the bittorrent protocol, a quasi-anonymous method favored by software and movie pirates. In an August 16, 2021, phone interview, Graham said those two system images can't be used to support the claim that Dominion has been wiping out evidence of a 2020 election hack:
The second image was a second computer. You can't even compare them.
Harri Hursti -- a Finnish internet security expert who famously demonstrated in 2005 how to hack a now-obsolete Diebold voting machine -- also said the files prove none of what is claimed. "Those are no evidence of anything being deleted from anywhere," Hursti wrote in a tweet embedded below.
My room of experts looking into the images here unanimously agreed that those are two images from two different systems - therefore those are no evidence of anything being deleted from anywhere. The logs and election archives were in separate folder outside images in the package.
-- Harri "scofield" Hursti (@HarriHursti) August 12, 2021
The devil is in the details
Lead Stories followed up with Hursti to learn the basis for his conclusions, for the benefit of experts who will want to check his work.
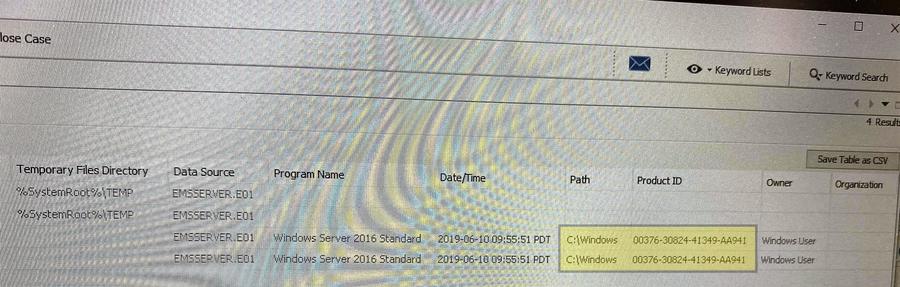
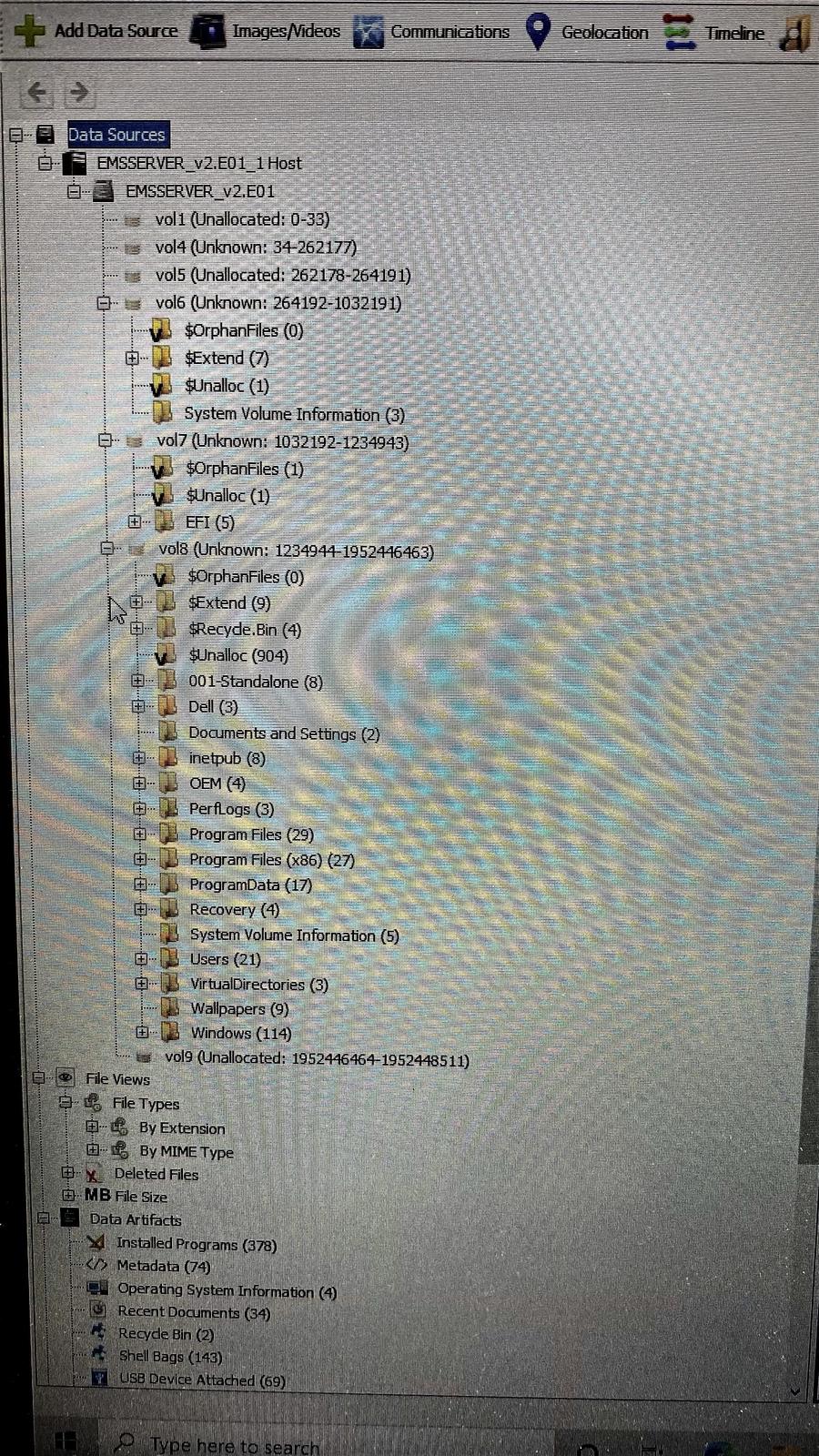
Three independent data points disprove the claim that data was deleted from Mesa County's voting and tabulation system, Hursti said in an August 18, 2021, phone interview with Lead Stories. The external drive used at Lindell's symposium to share the backup images held two folders: "colo data" held the two computer backup images, each about 20 gigabytes, while "EMSSERVER" was about 31 gigabytes and held logs, databases and other files in folders organized by election.
Hursti supplied cell phone photos he took when he was being allowed to see what was on the external drive, which are inserted in this fact check below:
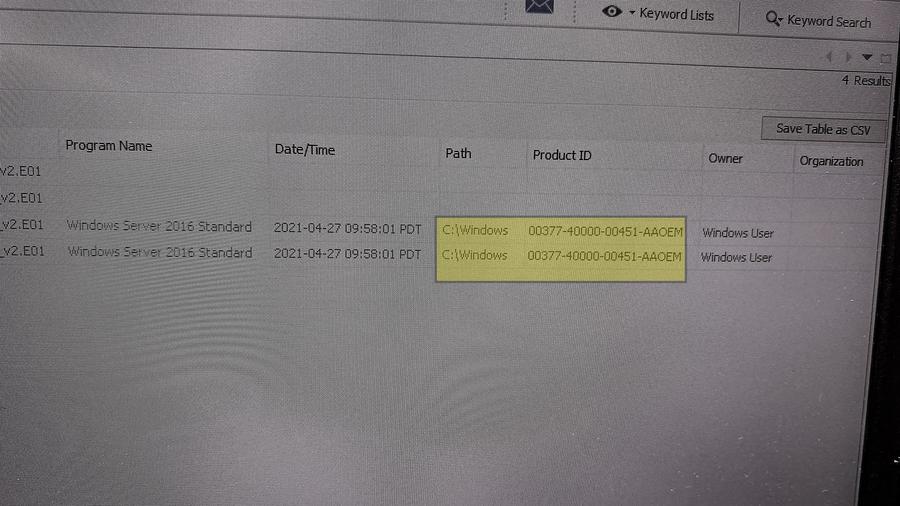
(Source: Harri Hursti photo of Product ID found in one of two backup images in "colo" folder)
(Source: Harri Hursti photo of Product ID found in one of two backup images in "colo" folder)
(Source: Harri Hursti photo of the directory of activity logs and election data folders found in the "EMS" backup image)
Hursti found in the "colo data" files that he could see the supposedly erased log files and election files in a directory (a folder of related files) on one of the computers that had been imaged:
The whole reason they were sharing the Mesa images was to claim that the Dominion/Secretary of State's update is deliberately deleting log files and election files. [But] that other directory already showed No, those files are here, they are not deleted, they are just outside of the images.
That directory was 31 gigabytes, when the images were about 20 gigabytes each. They [logs and election files] were already outside of the images in a directory, I think it was called 'EMS Server Election Database Export,' or something like that. That already proves that the point of files were deleted maliciously to be wrong.The second point which proves the files were not maliciously deleted is in the older one of the two images, where it has log entries that those files were copied to a mass storage device so that is almost certainly the log entries which was created when those files were copied out. That happened on 18th of May.
The third thing is it actually doesn't matter whether those two images are a different computer or not ... You cannot use one [image] to claim files were deleted because they are from different installations.
Hursti said that when you compare the software installation records in the two backup "images," it is clear each came from a different computer:
The older image has a partition table of three partitions and it is a traditional legacy boot, while the newer installation has nine partitions and it has an efi boot, a more modern version of the boot process. Also the partitions are a different size and everything else. It's fundamentally different.
The second place to look is to look inside the image and start looking, well what is the Windows product ID and license and you find that's different. So, if that would be a same installation, why would you have different Windows ID and product ID and license. That doesn't make any sense, either
Hursti's conclusions are supported by another cyber-sleuth who posted pictures of what he found in the computer backup files that were supposed to show Dominion was erasing computer files:
One indication I found: BIOS update logs.
-- TRAPEZOID OF DISCOVERY (@get_innocuous) August 15, 2021
On 4/27, a Dell 9FG85 BIOS update was run. The 9FG85 build is specifically for R640
On 5/25, (the update date), Dell H5DYH BIOS update was run. The H5DYH is specifically for T630.
These were both in the newer image (made 5/26) pic.twitter.com/wZW8nRzxGC
Graham said the problem for some of the less-experienced cyberanalysts at the conference is that their belief in the conspiracy theory clouds their thinking. He compared the search for nefarious activity in a torrent file to a search for a needle in a haystack. "There's always a lot of stuff you don't understand," he said. "For conspiracy theorists, things they don't understand are evidence of the conspiracy." Before people realized the two system images were not a before-and-after set, much was made of the fact that log files -- records of actions taken -- were missing. But he said when you dug in, you could find a new log entry showing those logs had been archived.
The closest Lindell got to releasing his promised "packet capture" evidence was a video loop showing masses of hexadecimal display of digital/binary data. Lead Stories, working from video of the data, established the video of the data was likely produced by Dennis Montgomery, who several Lindell allies have said is a peddler of fake data whose lawyer once called a "conman."
Updates:
-
2021-08-19T00:04:18Z 2021-08-19T00:04:18Z Updated to add phone interview with Harri Hursti.