After Mike Lindell's appearance on the April 28, 2021, "Jimmy Kimmel Live!" show, Lead Stories published a story titled "Attention Mike Lindell: What You May Want To Know About The 'Data' Used In Your Stolen Election Claims" that traced some of the data used in Lindell's movies to a man named Dennis L. Montgomery. Lindell has been quite vague on the source of his data and the name "Dennis L. Montgomery" never appears in any of his videos. And with reason: According to the New York Times, Montgomery's own lawyer once called him a "con man" and in the same article they also reported he sold non-functional terrorist-tracking software to U.S. security services as the War on Terror against al-Qaida was being waged by the George W. Bush administration. The Arizona Republic reported Montgomery once charged Maricopa County, Arizona, Sheriff Joe Arpaio for collection of evidence and that the sheriff's office then concluded "...Dennis Montgomery deliberately compiled massive amounts of data on to these drives for the purpose of obfuscating the fact the data itself contained no evidence..."
If the data Mike Lindell relies on as evidence came from Dennis Montgomery it wouldn't automatically mean it was false. But it would invite extra scrutiny and would require very thorough verification before it could be trusted. And as you can read in the article below, there are very good reasons to suspect Dennis L. Montgomery is not only the source for Lindell's data but even that he created the actual videos Lindell has been showing.
What did Mike Lindell say?
During the first day of Lindell's Cyber Symposium taking place from August 10-12, 2021, in Sioux Falls, South Dakota, Lead Stories asked Lindell by email if he could confirm on the record that Dennis L. Montgomery was not one of his sources as far as he was aware. He replied on the live stream that it didn't matter where he got it from. "I have it."
We also asked if he would agree that deliberately selling non-functional software to U.S. security services in the middle of the War on Terror and taking taxpayer money from Sheriff Joe Arpaio in exchange for fake evidence is unpatriotic and a dark stain on someone's reputation but we got not reply to that question.
Here is what we found:
Robert Graham, our cyber-expert who is present at Mike Lindell's Cyber Symposium, spoke with someone in Lindell's crew who identified himself as Joshua Merritt, a.k.a. "Spyder" or "Spider" (known for getting his name accidentally revealed by Sidney Powell). Here's what he reported back to us though chat messages:
I asked Spider, on the record, to clear answers: it comes from Montgomery, it's the source of those kiosk pictures and the packet captures mentioned in the videos, we have some bits that we can't decode or verify without the help of Montgomery,
It comes from Montgomery
It's the "proof" cited in those videos
Cyber experts will not be given the opportunity to verify it
He also tweeted about it:
34/ So I got some straight answers from Spider:
-- Robᵉʳᵗ Graham @ Sioux Falls cyber symposium (@ErrataRob) August 10, 2021
1. the data comes from Dennis Montgomery
2. it's the data shown in those Lindell videos
3. it's the hexdumps that have been scrolling in his videos and kiosk
4. we cyber experts will not be given opportunity to verify it pic.twitter.com/MqdvsFQ8qe
Mike Lindell has republished claims explicitly mentioning Montgomery as the data source
As we pointed out back in April, the data shown by Mary Fanning in Lindell's video "Absolute Proof" matches exactly with the data Fanning claimed on her own website "The American Report" (archived here) to have obtained from Dennis L. Montgomery and his website "blxware.org" and the associated "electionrecords.com". But in the movie she never says "Dennis Montgomery" and Lead Stories was unable to find any evidence of her directly telling Mike Lindell about the source of the data. Theoretically, Lindell could simply have been unaware and he could have genuinely believed he obtained the data independently through a different source.
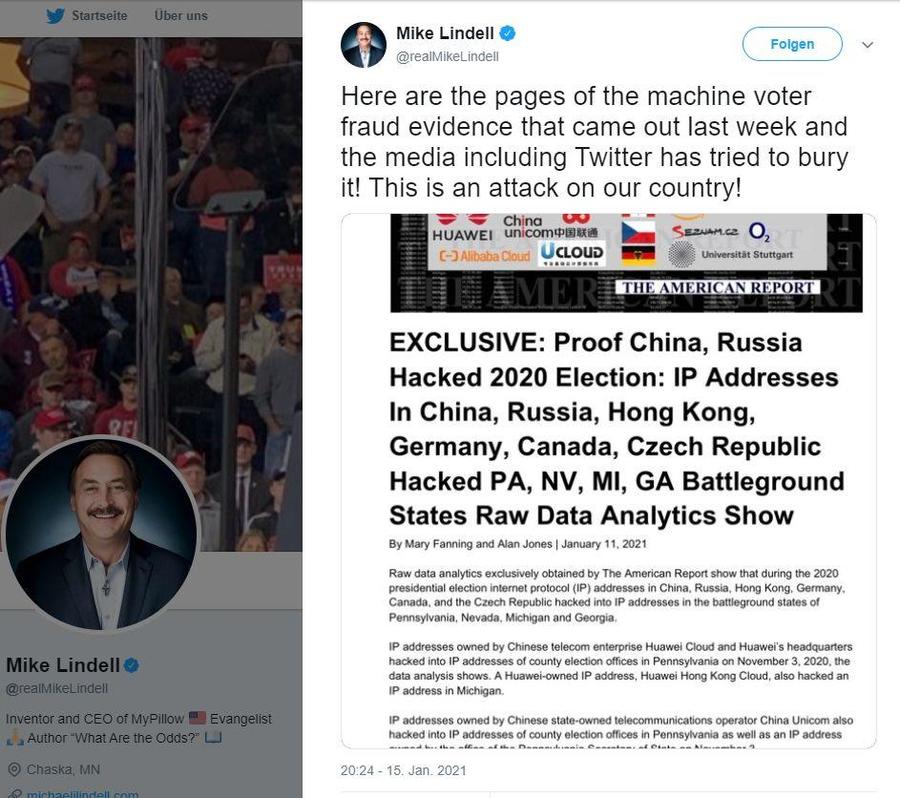
However on January 15, 2021, Lindell tweeted (from his now deleted Twitter account) a screenshot showing an article from The American Report (archived here) that links to the very same data on the very same "blxware.org" site.
(Source: Internet Archive screenshot taken August 9, 2021)
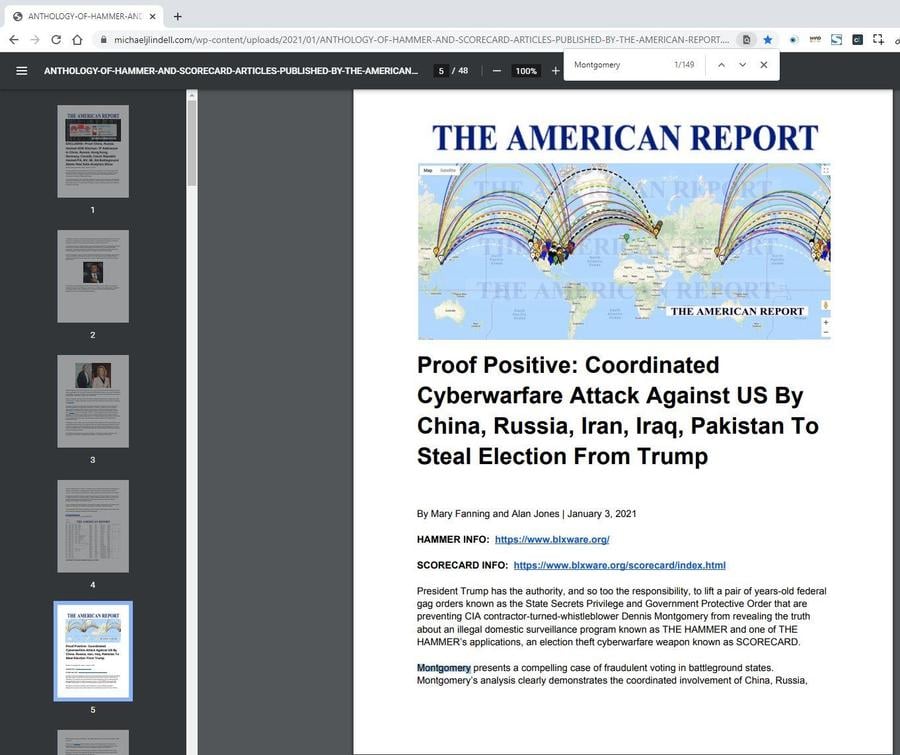
Not only that, but according to the Internet Archive's Wayback Machine as early as January 14, 2021, Lindell published a PDF file to his website michaeljlindell.com that contained no fewer than 149 references to Dennis Montgomery. It also had the same maps with colorful lines that were later used in Lindell's videos asserting the 2020 election was hacked.
(Source: michaelljlindell.com screengrab taken August 9, 2021)
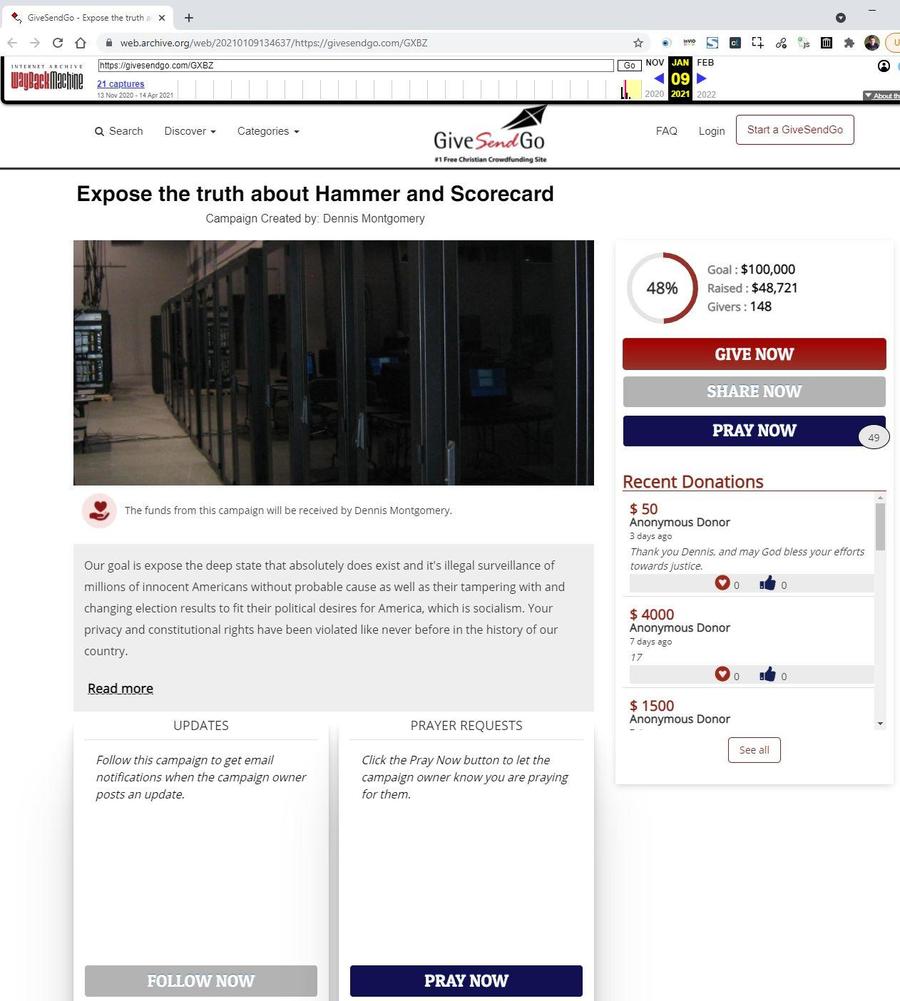
At the time both the blxware.org and electionrecords.com sites mentioned in the article had donation links that pointed to a GiveSendGo campaign for "Dennis Montgomery".
(Source: Internet Archive screenshot taken August 9, 2021)
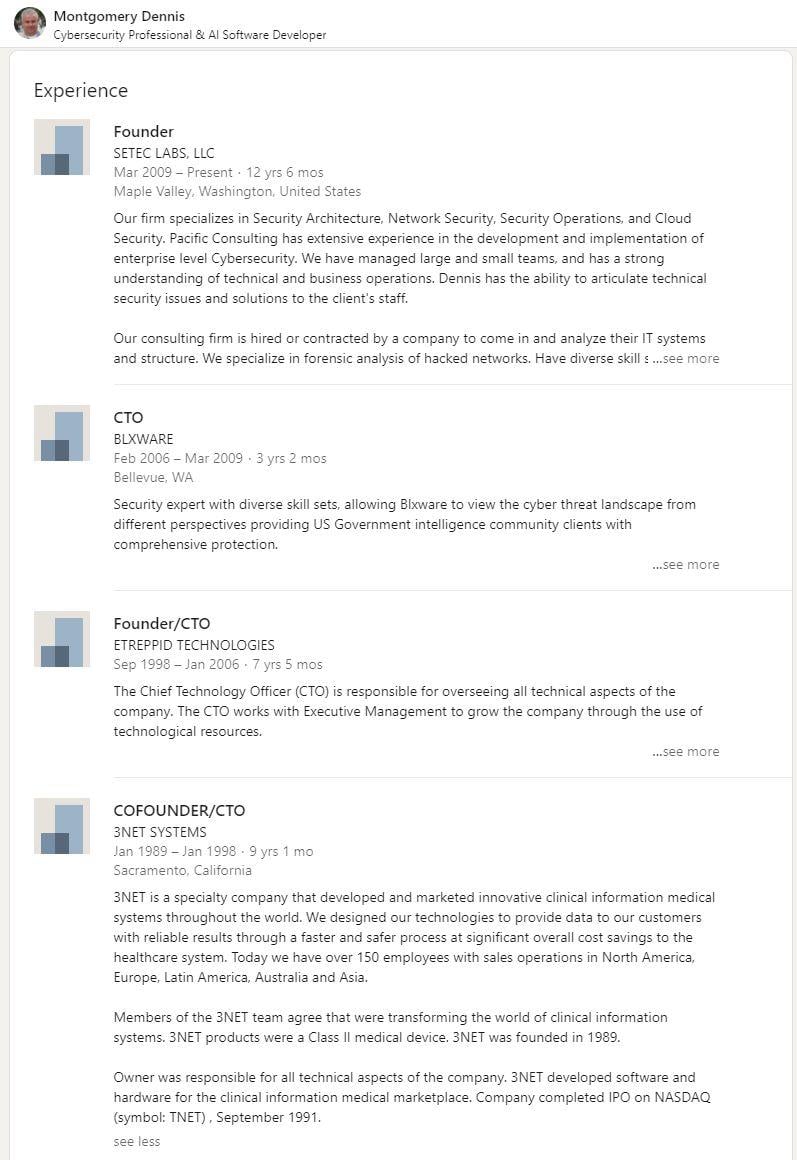
The blxware.org site also mentioned "3NET LABS", which, although it doesn't appear literally on a LinkedIn profile for "Dennis Montgomery" is still quite close to the "labs" in "SETEC LABS LLC" and the "3NET" in the "3NET SYSTEMS" that do appear in his list of professional affiliations and accomplishments.
(Source: LinkedIn screengrab taken August 8, 2021)
That makes it a lot harder for Lindell to maintain he was unaware of the Montgomery connection. At best, it means Lindell posted documents he called proof, and promoted website data sources without verifying who the apparent publishers were and before properly vetting them first.
More connections
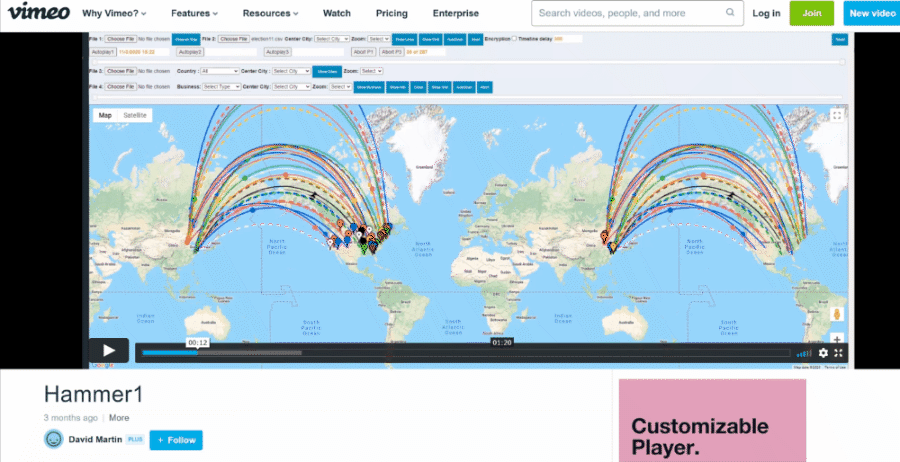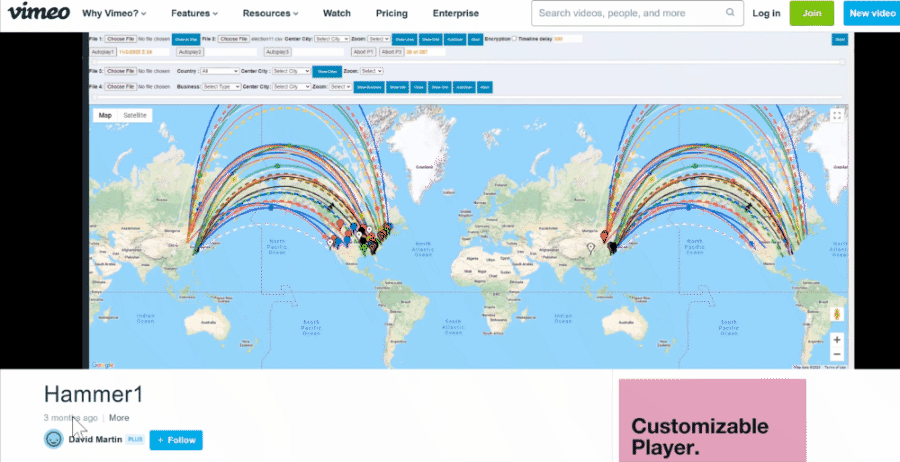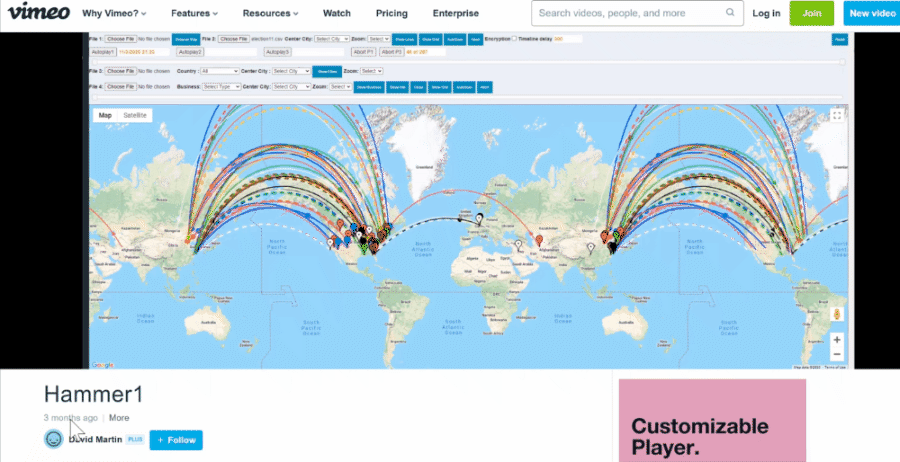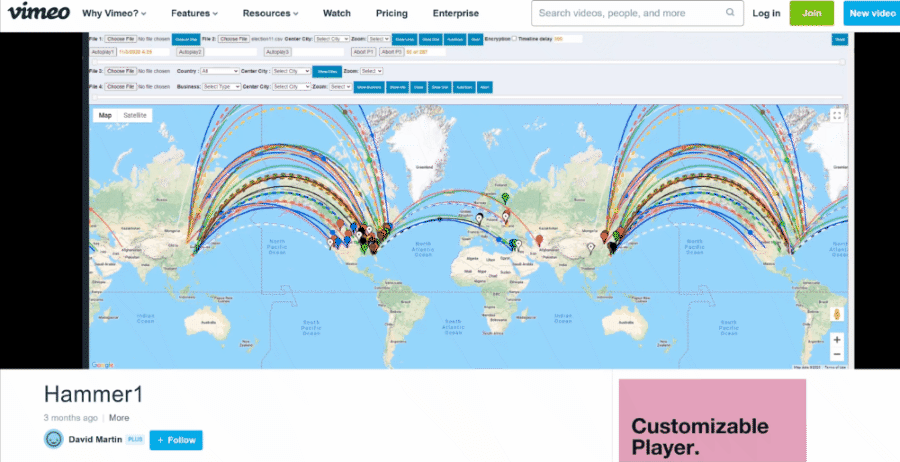
As we noted, the data on the electionrecords.com site also contained links labeled "DATE - PLAY VIDEO" and "ATTACK - PLAY VIDEO," which lead to two videos named "raw" and "Hammer1," hosted on the Vimeo video hosting service. Both were uploaded by an account named "David Martin" on January 29, 2021. These match the videos later also seen in Mike Lindell's movies. What follows are animated gifs we made to illustrate what the videos looked like at the time:
(Source: "David Martin" Vimeo account, GIFs of videos created Lead Stories from screengrabs taken April 30, 2021)
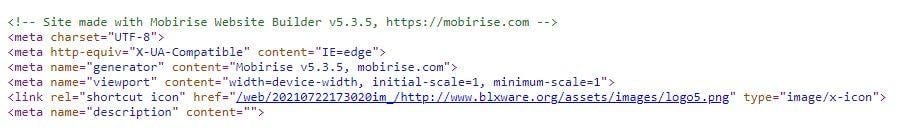
Review of the source code, shown below, of archived versions of the blxware.org and electionrecords.com sites on the Internet Archive's Wayback Machine revealed both were created using "Mobirise Website Builder":
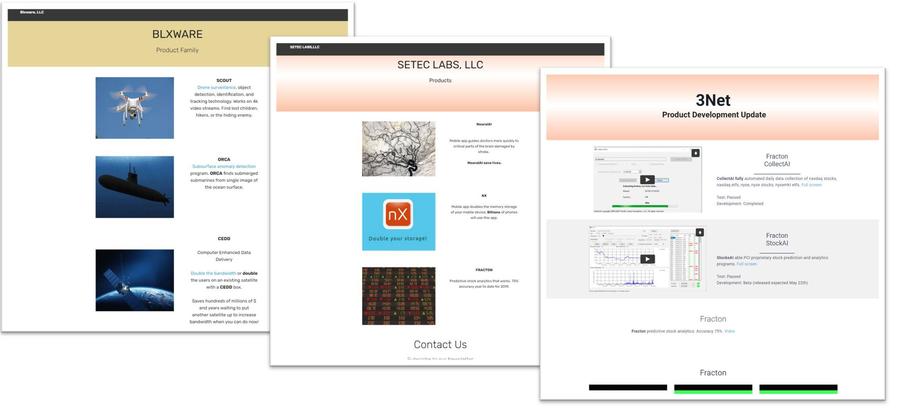
Lead Stories reviewed three websites of companies mentioned on blxware.org or on the Dennis Montgomery LinkedIn pages (blxware.com, seteclabs.org and 3netlabs.com, archived here, here and here) and found all three looked quite similar because they were all built using the same website building software. All three sites made heavy use of embedded Vimeo videos (on accounts named "jonjenkins" and "David"). Interestingly enough, the latest capture of blxware.org on the Internet Archive's Wayback Machine contained an embedded Vimeo video (ID: 551584241) with a clip from the "Law & Order" television show, a clip hosted on the "jonjenkins" account (archived here).
(Montage of Blxware, Setec Labs, LLC and 3Net web pages created by Lead Stories from screengrabs taken August 9, 2021)
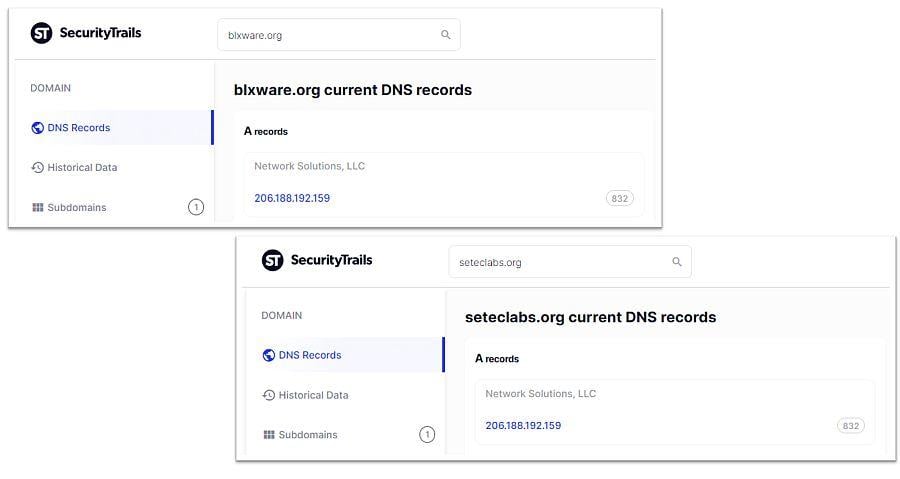
According to DNS data found via SecurityTrails here and here (archived here and here) and shown below in a series of screengrabs, the Setec Labs website and the blxware.org website (the one with the election data) were both hosted on the same IP address (i.e. on the same server on the internet).
(Source: Security Trails screengrabs taken Mon Aug 9 23:40:43 2021 UTC, displayed in montage created by Lead Stories.)
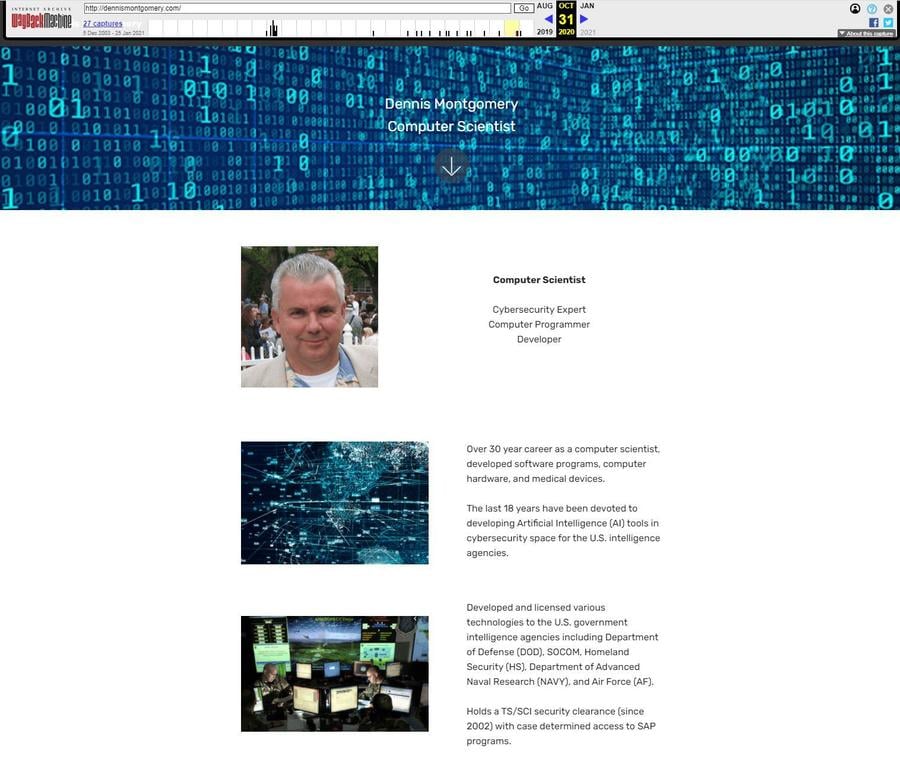
Note that a March 17, 2020 version of the 3netlabs.com website explicitly linked to the website dennismontgomery.com (archived here) using the link text "US GOV whistleblower. One man's 17 year journey..."
That site described Montgomery as a "Cybersecurity Expert", "Computer Programmer" and a "Developer" and it used the same photo found on his LinkedIn profile. Review of the source of the page also revealed it was built using Mobirise Website Builder.
(Source: dennismontgomery.com screengrab taken August 9, 2021 UTC)
Another site
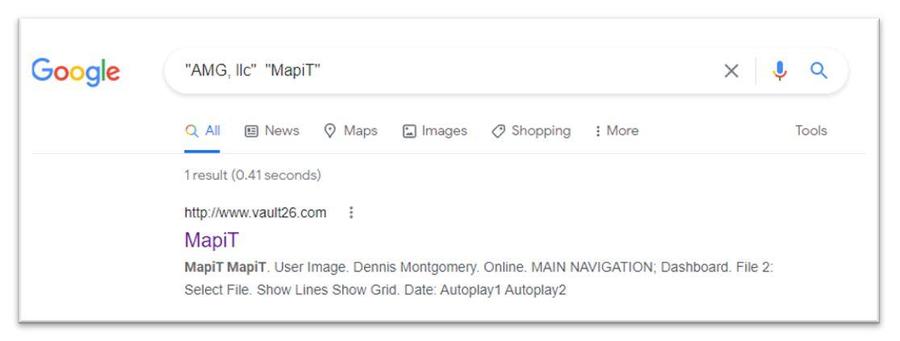
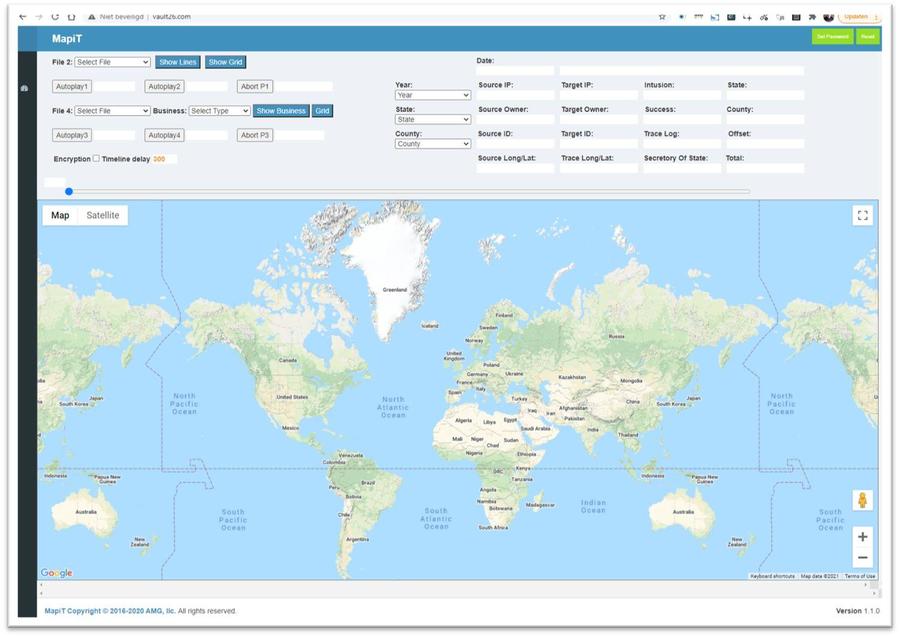
On June 17, 2021, Lead Stories received a tip from a source who preferred to remain anonymous who had been Googling "AMG, llc and "MapiT", which are three phrases seen in the earlier Lindell videos purporting to show animations of votes being stolen. The tipster had spotted similarities to graphics used in Lindell's videos and Montgomery's name was attached to them:
(Source: Google.com screengrab taken Aug 10 2021 UTC)
The only result that came back was a site named vault26.com (archived here) that looked exactly like the supposed software shown in Lindell's videos.
(Source: vault26.com screengrab taken Thu Jun 10 20:30:48 2021 UTC)
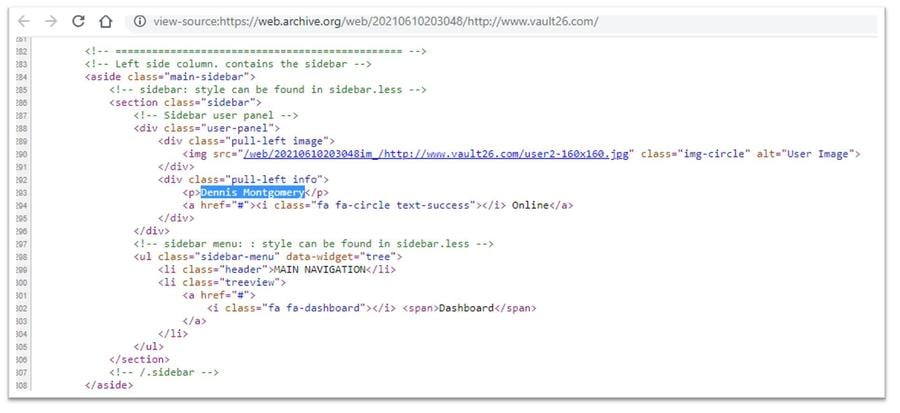
The HTML source code of that site contained the hardcoded name "Dennis Montgomery" in what looked like unfinished code to display in a sidebar which user is currently logged in.
(Source: vault26.com screengrab taken Thu Jun 10 20:30:48 2021 UTC)
More Vimeo videos
As we noted in our April 30, 2021, post about the sources of Lindell's data, the "David Martin" Vimeo account kept on publishing videos.
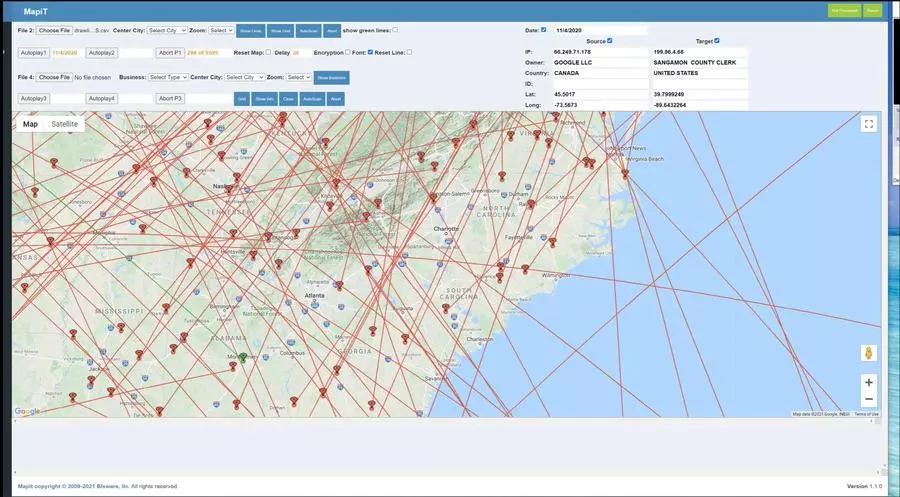
On April 29, 2021, it uploaded a new video named "wave4.mp4" (archived here):
(Source: vault26.com screengrab taken Fri Apr 30 13:52:42 2021 UTC)
In the bottom left corner you can see a copyright message that reads "MapIt copyright © 2009-2021 Blxware, llc" while at the top the application appears to be named "MapiT." Blxware is Montgomery's former company.
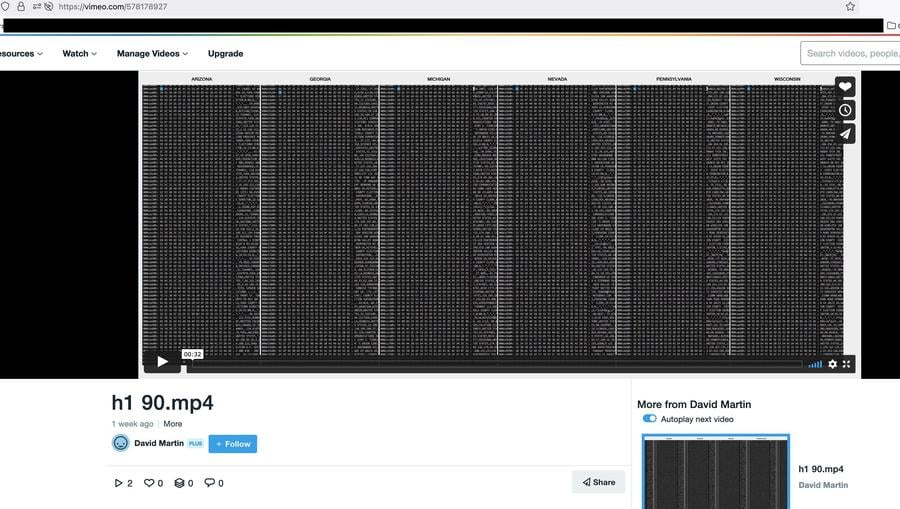
In July 2021 the "David Martin" Vimeo account started publishing videos showing the now familiar "scrolling pcap" data columns that Mike Lindell later also used at his Cyber Symposium. On August 10, 2021, Lead Stories published a manual on how videos like these can be easily and cheaply produced along with the likely reason what they show are not packet captures.
(Source: vimeo.com screengrab taken early August 2021)
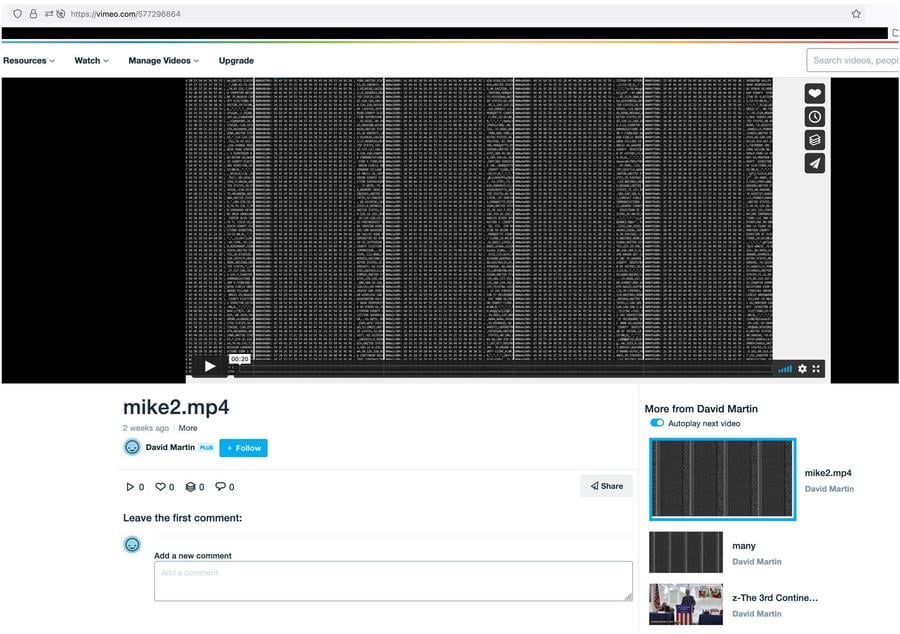
One of the videos was even named "mike2.mp4", perhaps hinting at the intended recipient or audience:
(Source: vimeo.com screengrab taken early August 2021)
Lead Stories took screenshots and downloaded all the videos present on the account. You can see a giant screenshot showing thumbnails for all the videos on the account here, or a smaller sample right here:
(Screenshot of the "David Martin" Vimeo.com account, taken August 4, 2021)
Sites and account going down ahead of Mike Lindell's Cyber Symposium
Lead Stories feared the website blxware.org and the "David Martin" Vimeo account would be taken down and we were proven correct. At the time of publication blxware.org shows an error message and so does the link to the David Martin account on Vimeo. The website dennismontgomery.com was briefly down on August 9, 2021, but appears to be up again as of this writing on August 10, 2021.
But blxware.org is still available via the Wayback Machine as we showed before, and we took screenshots and downloaded all the videos of the Vimeo account. On Monday, August 9, 2021, we generated SHA256, SHA512 and MD5 hashes for all the files we created and downloaded and posted proof for that on Twitter:
Publishing hashes of files proves the files the hashes were based on existed on the date of publication.
-- Lead Stories (@LeadStoriesCom) August 9, 2021
Here are some hashes of files we might release at a later date. The date on this tweet serves as the proof we already had these files today. pic.twitter.com/P5pa1qcccc
The hashes for the full-sized screenshot we posted here are as follows if anyone wants to check:
- MD5: 3E1E08644A0EB830B6C55EF8908EF231 FireShot Capture 010 - David Martin - vimeo.com.png
- SHA256: 56FA4237E71C05788B73EEB06442F64A1189F103F10C8D1C79CA0979ACBD5D5F FireShot Capture 010 - David Martin - vimeo.com.png
- SHA512: CA65F6CB2C73E9EC655619AA6CD8A3F38936749C165D7CF5F53515A69955B69D587197A3999F92FF9265FCEC50A9DB7BD860A136E4877CACB424A95E3F6D93DE FireShot Capture 010 - David Martin - vimeo.com.png
What this means
None of the above means it is 100% certain Dennis Montgomery had a hand in creating the data Lindell is using to allege the 2020 presidential election was hacked. It should, however, give anyone pause that there are so many links between Lindell's data and a man with a history of providing fake evidence and facing accusations of falsifying demonstrations, a man called a "con man" and a "known fraudster" by Lindell allies like David J. Harris Jr. and The Gateway Pundit.
We attempted to contact Montgomery in early 2021 to ask about all this when we first saw the many mentions of his name in connection with this evidence, but never got a response. We attempted again via the contact form of his website at the start of the Mike Lindell Cyber Symposium on August 10, 2021, and we will update this story if we get a reply this time.
But to use an analogy: this is like finding a suspect standing over a dead body, smoking gun in hand, while wearing a nametag and matching the description of an escaped serial killer. There still is the possibility of an impersonator or an evil twin brother, but the defense counsel is going to have to put in a lot of work to collect enough evidence to convince a jury he didn't do it.
Mike has seemingly decided to ignore the issue entirely.