STORY UPDATED: check for updates below.
Did the materials released by Mike Lindell at his Cyber Symposium meet evidentiary standards of relevance, proof of origin, chain-of-secure-custody and reproducibility that online security experts say would be needed to take seriously his claim that he holds massive data files showing the 2020 election was stolen by hackers? No, that's not true. Lead Stories asked for the information necessary to authenticate his evidence two weeks in advance of the symposium and was rebuffed, and the materials released August 10, 11 and 12, 2021, were more of what Lindell showed before the gathering: videos showing computer code of unauthenticated origin scrolling in a continuous loop.
During the weeks leading up to the Cyber Symposium, Lead Stories staff talked to Lindell, his anonymous designated spokesperson and national election security and cybersecurity experts to double-check what would be needed to verify that Lindell has what he claims he has. We boiled it down to nine questions.
The following chart summarizes the queries by which we are testing his data and our findings so far and it may be updated when or if Lindell and his team provide the information requested. The version currently displayed shows no changes since August 10, when it was posted.
Before the symposium opened, Lindell and an unnamed caller he identified as his cyber expert would not answer any of the nine queries, none of which had been addressed in four online videos Lindell released.
Lead Stories arranged to send to the symposium Robert Graham, a cybersecurity expert well known for inventing several internet security tools. Graham on August 10 and 11 examined Lindell's materials and consulted with us in judging the reliability of the data Lindell released. As of the conclusion of the symposium, Graham said he still had not received a full copy of the "pcap" data Lindell says holds the evidence of election fraud. In a series of tweets from the floor of the symposium, Graham included the hashtag: #ReleaseThePacketCaptures
Here are the tests listed in the chart:
Is there a full and detailed explanation of who created these "data files" including an explanation of how and where they intercepted the data, in enough detail (who, when, where) that it can be confirmed?
Rating: Refused/No Answer Given 
During the August 10 session of Lindell's gathering, Lindell declined to reveal the source of his data, saying "It doesn't matter where you get it from. I have it." On August 12, there was no release of the files at the heart of Lindell's four videos.
Lead Stories has published, in this fact check, multiple clues showing Lindell's data likely was generated by Dennis L. Montgomery, a Florida man reputed to have sold fake data both to the U.S. Department of Defense and to Maricopa County, Arizona, Sheriff Joe Arpaio. According to the New York Times, Montgomery's own lawyer once called him a "con man" and in the same article, the Times reported Montgomery convinced the Defense Department his software could find secret terrorist messages in Al Jazeera broadcasts. The Arizona Republic reported Montgomery once charged Arpaio more than $100,000 to collect evidence of a judge's conspiracy against Arpaio and that the sheriff's office then concluded "... Dennis Montgomery deliberately compiled massive amounts of data on to these drives for the purpose of obfuscating the fact the data itself contained no evidence ..."
Ahead of the symposium, neither Lindell nor his designated spokesman (identified only as a cyber expert) would give the name of the person who assembled his data, nor how they intercepted it, nor where nor when. This makes it the equivalent of hearsay evidence, which gets tossed out of court because when the origins of information cannot be examined, the evidence cannot be granted the full weight that adheres to evidence backed by people and methodology that can explain where it came from.
A very well-supported criminal or spy might be able to intercept the amount and type of data described by Lindell, according to Greg Miller, a computer scientist and lawyer who is chief operating officer at Open Source Election Technology Institute. The Institute's team of engineers and lawyers develop technical solutions for election integrity. He said those capable of capturing and unencrypting the amount and type of traffic Lindell claims to have would have to be one of four types:
- A law-breaker working in one of the big ISPs (internet service providers like AT&T);
- The intelligence service of an adversarial nation like Russia or China;
- A law-breaker violating the secrecy rules of the National Security Agency or other U.S. intelligence agency;
- The U.S. government itself.
"Anyone doing this would be a criminal," Miller said during an August 5, 2021, briefing for Lead Stories. "There's no way they could get access to the river of data." And, he said, traffic across the internet does not contain official vote tallies. "Never," he said. "It does not happen."
He said Lindell's claims are predicated on a fundamental misunderstanding of how individual precincts and counties deliver their vote tallies to their states. "Data from these machines ends up on a data stick or other removable media," he said. "It's not transacted across public TCP/IP networks." He said the few places that don't hand-deliver data media use private networks and none of those places are in contested states.
Day 3 Update: Robert Graham, the cyber expert sent to the event by Lead Stories, heard from Joshua Merritt (a.k.a. "Spyder" or "Spider"), a member of Lindell's crew, that the data indeed came from accused con man Dennis Montgomery as we suspected. Merritt's statements later seemed to be confirmed by The Gateway Pundit and the Washington Times. However, the Washington Times later added:
Kurt Olsen, a lawyer on Mr. Lindell's team said there were multiple sources of the data that Mr. Lindell claims to have, and did not confirm that Mr. Mongtomery was the source of the data. He also clarified that the $5 million challenge has not been canceled and that Mr. Merritt would not be privy to that information.
Clarification: The article previously described Mr. Merritt as Lindell's lead cyber expert. Mr. Merritt is a cyber expert on the red team hired by Mr. Lindell to interrogate the data for the symposium, and does not work directly for Mr. Lindell.
We asked Lindell several times to confirm or deny that Montogmery was the source but received no reply.
At the end of the symposium no concrete information had been provided about where the pcap data supposedly originated from, who collected it or how.
Is there a full and detailed description of how Lindell's sources were able to decrypt the contents of the packets, including details that answer plausibility questions (access point, petabyte hardware used, software used).
Rating: Refused/No Answer Given 
At the August 10, 2021, session of Lindell's Cyber Symposium, the evidence provided was video of scrolling lines of hex dump representations of digital data, but those speaking from the stage attributed the work to unnamed "cyber experts," and the access point, hardware and software used was not revealed.
Election and internet security experts Lead Stories consulted ahead of the symposium said it would take someone with access to a giant data stream and with the training and experience to run powerful software applied to processing of petabytes of data.
Miller said the internet traffic interception and decrypting Lindell describes would require huge computing resources capable of handling petabytes of data in real time. The person performing the surveillance would need to be intercepting one of the principal fiber optic cable data routes, called the internet backbone, in which the fastest routers deliver data at 100 gigabytes per second. While people in his field of work worry about such a hack, none has been proven. "These are legitimate concerns about technology infrastructure that have been weaponized to claim something that didn't happen."
He said election and internet weaknesses, discovered during Russia's 2016 attempts to hack the U.S. election, have been closed. "A lot of effort was put in place to plug those holes, to greatly reduce that attack surface," he said.
Day 2 update: No updates here.
Day 3 update: No updates here.
Did Lindell provide a practical demonstration of interception and decryption of packets sent between two Lead Stories-controlled servers to serve as proof these experts at least have the skill and access required to do what they claim they can do?
Rating: Not Answered Yet 
Ahead of the symposium, Lindell declined to give Lead Stories the opportunity to run its own independent-of-Lindell test of the hack he claims he has documented.
At the August 10, 2021, session, a model election was staged, using voting machines, but no demonstration of interception and decryption of voting machine or tallying machine was offered.
Day 2 update: No updates here.
Day 3 update: At the end of the symposium no practical demonstration was offered of real, live packet interception over the open internet on the massive scale that would have been required to capture the data Mike Lindell claimed to have.
Were observers given a complete downloadable version of all files, preferably signed/hashed so we can verify our version is the same and nothing got garbled in transit?
Rating: Refused/No Answer Given 
A data set that is signed or hashed uses a computer security algorithm that characterizes a file mathematically so that the sender can be sure what is received is what was sent, or so that duplicates can be compared to ensure they are identical.
In advance of the symposium, Lindell declined to provide a full set of his files, which he says are a massive copy of "packet captures" (pcaps) of internet traffic that prove China hacked the election, saying he will only provide them to the U.S. Supreme Court.
Cyber security expert Graham, attending the conference to assess the data, finished the August 10 session of the conference with a series of tweets complaining he had not received the promised pcaps and launching a hashtag: #ReleaseThePacketCaptures.
33/ This is incredibly frustrating. Lindell invited "cyber experts" and "fact checkers" to come and confirm the "packet captures" -- and has yet to provide us any packet captures and it's 4pm already. #ReleaseThePacketCaptures
-- Robᵉʳᵗ Graham @ Sioux Falls cyber symposium (@ErrataRob) August 10, 2021
Day 2 update: Graham reported no pcap files were distributed to the cyber experts today either.
56b/ I mentioned this because some of his PR guys came by looking to take video of cyber experts working on packet captures. They seem confused by the fact that theres no cyber experts who have seen the promised packet captures.
-- Robᵉʳᵗ Graham @ Sioux Falls cyber symposium (@ErrataRob) August 11, 2021
He did say some new files were offered up that were alleged to be images of a Dominion server from Mesa County in Colorado. But no explanation was offered as to how these were obtained other than that they were downloaded from a "public link."
57/ To be fair, the "cyber experts" are indeed working on NEW data, like the system images shown on stage. So they are working.
-- Robᵉʳᵗ Graham @ Sioux Falls cyber symposium (@ErrataRob) August 11, 2021
It's just that no "cyber expert" at the conference is working on the OLD pcaps or proof from his Absolute Proof video.
Day 3 update:
None of the promised pcap files were provided to the cyber experts.
72/ So they had one of the "cyber experts" go on stage and describe the conclusion of the group. I didn't hear precisely what was said, but my conclusion is simply: we didn't get the Absolute Proof packet captures that show the flipped votes that Mike Lindell promised.
-- Robᵉʳᵗ Graham @ Sioux Falls cyber symposium (@ErrataRob) August 12, 2021
75/ Instead of giving us the data we were promised, the Absolute Proof of votes being flipped, Lindell dumped a bunch of new data on us, like Mesa county disk images they got yesterday. Yes, of course, that needs a lot time to search for things and analyze.
-- Robᵉʳᵗ Graham @ Sioux Falls cyber symposium (@ErrataRob) August 12, 2021
79/
-- Robᵉʳᵗ Graham @ Sioux Falls cyber symposium (@ErrataRob) August 12, 2021
Final verdict of this "cyber expert":
Number of "packet captures" or "cyber pcaps" seen = 0
Amount of "Absolute Proof" seen = 0
Amount of any evidence seen = 0
Is there a full and detailed description of the exact attacks the pcap files purportedly show (i.e. what software was attacked and on what type of equipment, which exact weaknesses were exploited, how exactly was data changed on the target machines?), preferably with steps included to reproduce the attacks and/or copies of bug reports submitted to the software vendors?
Rating: Not Answered Yet 
Lindell's response to Lead Stories' request for detailed timelines or narratives of the attacks he says are documented in his pcap files was, before the symposium, that we'd have to wait for the symposium.
At the first day of the symposium, details of the exact hacks were not provided, only a claim that election hardware and software was attacked in all 50 states.
Day 2 update: No updates here.
Day 3 update: No definitive evidence or description was provided of specific attacks or intrusions seen in the pcap files, since the pcap files were not released.
Three people (among them Draza Smith and Mark Cook) were brought onstage to present the results of several mock elections that were held on fictitious "Minion" election equipment created for the occasion that consisted of a scanner and what were described as an election management system and a counting machine plus a router to connect them all together. The demonstration purported to show a hacker changing the final vote tally by sending SQL commands to the server keeping the tally.
What the demonstration also showed was that it required stuffing extra paper ballots in order to make the hacked tally match up to the number of votes on the ballots.
However, no evidence was offered beyond speculation that any of this happened in reality or that it would even be possible for such SQL commands to be sent to actual election systems over the internet (as this would require the correct login information for the database and an internet connection). As one of the panelists admitted in response to an audience question, they had not been given any of the packet captures Mike Lindell supposedly had that would prove any of this.
Is there a full and detailed explanation of how these changes remained undetected even in places where paper ballots were later hand audited. If this explanation requires complicity of local officials, were they named, with proof provided?
Rating: Not Answered Yet 
With paper ballots in hand, auditors would quickly and easily spot election fraud the way they spotted human error that resulted in a temporary miscount of preliminary unofficial tallies.
Douglas Frank, a chemistry Ph.D. whose claims of statistical anomalies in election data are featured in a Lindell video, said at the August 10, 2021, session of Lindell's symposium that he presented evidence of the hack to the senior staff of the Ohio Secretary of State's office and they ignored him.
The spokesman for the office of the Ohio Secretary of State told Lead Stories in an August 10, 2021, phone interview that is not true. In a follow-up email, Rob Nichols wrote:
"The Secretary of State's staff met with Dr. Frank for nearly two and a half hours ... Dr. Frank acknowledged that he did not possess any evidence to prove his theories about irregularities in the 2020 election, or any previous elections which he also claims were tainted. As always, our office will continue to aggressively pursue any credible allegation of fraud in any election ..."
The lack of a paper trail of the alleged hack is a major weakness in Lindell's claims, election security experts told Lead Stories.
There are worrisome aged computing systems used in elections that could be hacked, says Professor J. Alex Halderman, of the University of Michigan electrical engineering and computer science department. He has been called as a witness in congressional hearings on election integrity and serves as an expert witness in major court cases. Paper ballots are used by almost all U.S. voters, he said. In an August 6, 2021, briefing of Lead Stories staff, Halderman said paper ballots make it extremely hard to hack an election the way Lindell claims was done. "It's kind of a low bar to disprove there is error or fraud in reporting. You just have to go look at the numbers," he said. There are a few areas that use touch-screens, but so few that it would be what he called a very small target for hackers.
Halderman said Georgia looked at a large enough sample of paper ballots to rule out election tampering, and yet Lindell continues to claim a 50-state hack changed the outcome of the Trump-Biden race.
Miller, too, said paper ballots make Lindell's claims into nonsense because the data sticks with preliminary local tallies are backed up by paper reports, which are backed up by the paper ballots themselves, which can be recounted to check the digital reports. "Prove to me that original paper ballots are altered or destroyed," Miller said.
Day 2 update: No updates here.
Day 3 update: During the "mock election" demonstration the theory was floated that electronic hacking happened in combination with paper ballot stuffing in order to remain undetected. No explanation was offered on how the thousands of people needed to add correctly marked extra paper ballots all over the country would be organized and coordinated, to say nothing of pulling off the massive falsification of voter registration list needed to make sure the number of ballots remained consistent with the hacked tally and lower than the number of registered voters. As we noted in this question, it would be nice to have some named suspects and evidence in such case, not mere speculation.
The demonstration was offered as a reason to get rid of all electronic counting equipment and to rely on paper ballots exclusively. It remained unclear how that would fix the paper ballot stuffing problem implied by the demonstration. In fact, getting rid of the electronic equipment in this scenario would make it easier for paper ballot stuffing to remain undetected since it would completely eliminate the need for hacking to make the electronic tallies match up with the paper ballots.
Do the pcap files show if votes were flipped, stolen, injected, added, cloned or duplicated (or something else, or all of them) and what that means for contradictory claims?
Rating: Not Answered Yet 
Prior to the symposium, Lindell declined to provide details. At the August 10 session, the master file of pcaps was not released for examination.
Day 2 update: No updates here.
Day 3 update: Since no pcap files were provided, it remains unclear if votes were supposedly flipped, stolen, injected, cloned or if some other method was used. However, as this fact check shows, the "corrected" election results Lindell showed directly contradicted the theories about ballot injections offered by Dr. Douglas G. Frank from the very same stage.
If the pcaps show the attacks were a mixture, is an explanation given as to why election thieves risked undoing each other's work by stealing, flipping the same batches of votes?
Rating: Not Answered Yet 
There are logic problems with conflicting claims by people affiliated with Lindell. If all methods were in use, they might have cancelled each other out. Since Lindell alleges a widespread and sophisticated attack on the election, Lead Stories has asked why potentially self-cancelling methods were used.
At the August 10 session, Lead Stories' question was not answered, although Douglas Frank's statement -- that hackers inflated voter registration lists with fake names in advance of election day to give them a pool of made-up voters -- would make other forms of fraud difficult if flipping, stealing, injection and adding tactics were all being used at the same time.
Day 2 update: No updates here.
Day 3 update: No updates here.
Is there an explanation why, if this pcap evidence was acquired before Trump left office, when recounts and lawsuits were underway, it was withheld from public view until now?
Rating: Answer has issues
Lindell has described, in the videos in which he has claimed to know how the election was stolen, a massive real-time data stream that shows votes being swapped. If that's true, why wasn't that data presented to the Trump administration in the month following the election? Why wait 10 months to share it (if indeed it will be shared in full)? Lindell, prior to the symposium, declined to answer.
At the symposium on August 10, Lindell said he didn't go to the FBI because the William Barr-led Justice Department was part of a false narrative that the election was not tainted with significant fraud.
Election security experts have been privately critical of Lead Stories, saying the fact check agency has fed into a fantasy debate by engaging with Lindell's claims, which some security experts say are implausible. The experts and state election officials say voting and tallying machines are not connected to the internet. That makes impossible a real-time hack of the kind Lindell describes. Results are either delivered to statewide tallying centers by hand or, in rare cases, delivered via private networks not connected to the internet.
But, since Lindell's claims get wide circulation and we can't prove no one violated professional election procedures by finding a way to plug voting machines into the internet, we consulted experts to verify what would be needed to prove the hack that Lindell alleges.
Day 2 update: No updates here.
Day 3 update: No updates here.
Election and cybersecurity experts say Lindell's claim is "science fiction"
In addition to attending the symposium where Lindell promised all would be revealed, Lead Stories consulted with a variety of elections experts and looked for published expert analysis of Lindell's claims. Here's what we learned:
Lindell's claims are "based on science, with fantasy and supposition on top of it," says Halderman, who is viewed in the election security field as a bit of a doomsayer, for his 2016 analysis that suggests it's possible that election could have been hacked in some parts of the country. "It's not completely crazy that serious attacks could take place," he said, but added "They [Lindell and his sources] haven't been able to produce a shred of credible evidence that such a thing occurred."
Lindell's claim is extraordinary and would require credible evidence, which had not as of the August 6 briefing been shown. "You're making a bold claim," Halderman said. "It requires extraordinary evidence. Pony up."
A lawyer trained in software engineering, Open Source Election Technology Foundation (OSET) founder Greg Miller, said exploitable entry points identified after the 2016 election were closed by 2020 and that's one reason Lindell's claims are impossible.
CISA called 2020's election "the most secure in American history," noting there were paper ballots to back up every tally and that hackable entry points had been identified and closed.
When states have close elections, many will recount ballots. All of the states with close results in the 2020 presidential race have paper records of each vote, allowing the ability to go back and count each ballot if necessary. This is an added benefit for security and resilience. This process allows for the identification and correction of any mistakes or errors. There is no evidence that any voting system deleted or lost votes, changed votes, or was in any way compromised.
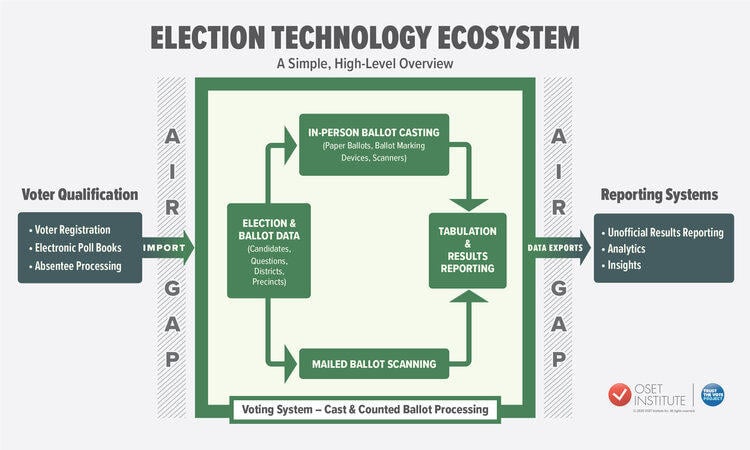
Miller's organization, OSET, works with election officials in multiple countries to improve the security of elections. The organization uses this graphic to illustrate how unlikely a hack is. The "Air Gap" indicates how standard election systems are insulated from the internet to prevent exactly the kind of hacks Lindell claims happened.
Lead Stories' cybersecurity adviser, Graham, said that in his experience as a "white hat hacker" who tests security systems by hacking as deeply into them as he can, such diagrams do not often show the true state of security. But, he acknowledged that being able to audit paper ballots makes Lindell's claims unlikely.
During the 2020 campaign, it was Graham who used DomainKeys Identified Mail (DKIM) signatures to authenticate, for the Washington Examiner conservative news site, leaked emails between Hunter Biden and an advisor to the Ukrainian petroleum company Burisma, thanking Hunter Biden for an introduction to his father, Vice President Joe Biden. The elder Biden was at that time in charge of U.S.-Ukraine relations and supporters of Trump said they were proof of corruption or at least poor judgment on the part of both Bidens.
Graham created the BlackICE personal firewall, the first network intrusion prevention system (IPS), and is a frequent speaker at network security conferences. He holds CISSP certification, the top-level cybersecurity exam for experts.
Updates:
-
2021-08-11T22:51:03Z 2021-08-11T22:51:03Z Added Day 2 updates. -
2021-08-09T17:56:22Z 2021-08-09T17:56:22Z This chart in this fact check will be updated August 10-12, 2021 as new information is released and analyzed.