Mike & Dennis
At Lead Stories we have a long history of looking at Mike Lindell's election fraud claims. Readers will remember our fact checks about Lindell's four conspiracy-filled election fraud "documentaries" here, here, here and here, or our coverage of his Cyber Symposium here. We also warned him about Dennis Montgomery, a man with a long history of providing fake evidence, and about accusations against Montgomery of falsifying technology demonstrations who has even been called a "con man" and a "known fraudster" by Lindell affiliates with their own MyPillow promo code like David J. Harris Jr. (site appears to be down, but archived here) and The Gateway Pundit (archived here).
Lindell claims he got 32 terabytes of data from Montgomery that allegedly show internet traffic recorded during the election that would prove the 2020 U.S. presidential election was hacked by China (or someone else, claims have also included Russia, North Korea, Iran, Iraq and Pakistan at various points). Lindell has never made this data public despite saying on November 2, 2022, (archived here -- 24:14 in) that a gag order had been lifted that prevented him from sharing the data. As Lindell said in the video: "Yesterday ... the United States government said ... this data from Dennis Montgomery, of the election, is good to go. You can show it to the world."
At the time of writing Lindell still hasn't shown the data to the world, although he did claim in a video (archived here) posted on July 14, 2023, that he gave it to Dominion and Smartmatic. At about 2:17 in the video Lindell says: "We've given the 32 terabytes to Dominion and Smartmatic in those lawsuits." Later in the video he claims he is still trying to get the gag order lifted, despite his earlier pronouncements. That seems to indicate Lindell still has not lost faith in Dennis Montgomery.
Election Crime Bureau
On August 18, 2023, the Daily Beast reported that Lindell announced a plan to fight voting fraud that involved a scanning device and a new website:
During the Thursday symposium (called the 'Election Crime Bureau') in Springfield, Missouri, Lindell touted the benefits of his new 'wireless monitoring device' (WMD), which he said can scrape data on nearby devices with internet access like phones and computers. If the device is in a polling place, and it sees a new device come online, that could be proof of a Chinese plot to hack the building and toggle a few more votes away from Republicans.
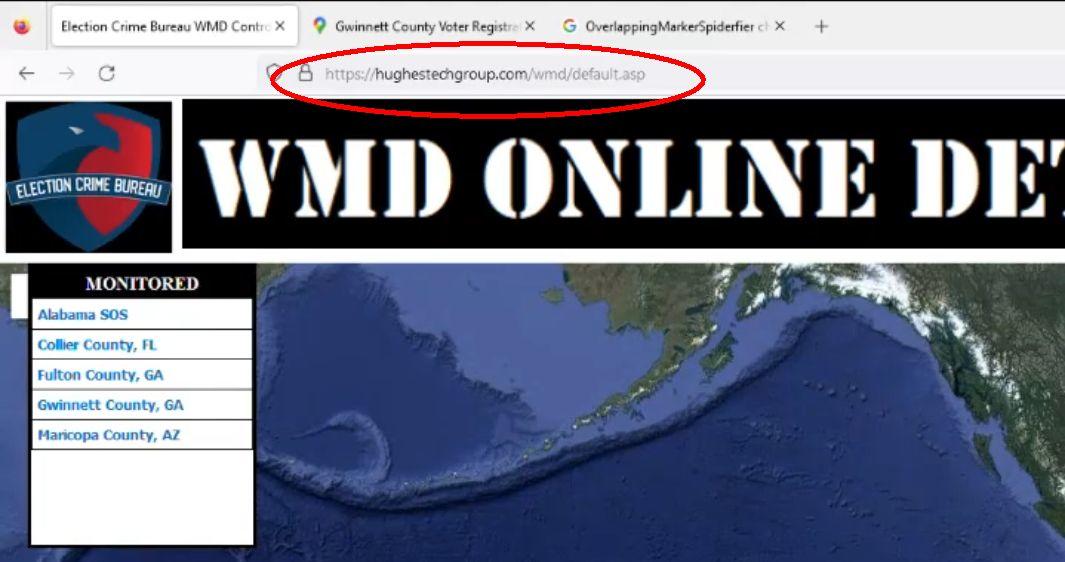
The data scraped by the device would supposedly be displayed on the website https://electioncrimebureau.net (named the "WMD Online Detection Viewer", archived here). However in the video that was posted on FrankSpeech on August 16, 2023, (archived here) to explain how it all worked, eagle-eyed viewers could clearly see the original URL of the website: https://hughestechgroup.com/wmd/ (archived here). Note that a few hours after we sent emails to Mike Lindell and others asking for comment both sites started redirecting to https://electioncrimebureau.com (with .com instead of .net) but the archived copies we linked to in this article still work.
(Source: screenshot of https://frankspeech.com/Video/mike-lindell-introduces-wireless-monitoring-device-to-secure-elections taken by Lead Stories on August 24, 2023)
It appears both electioncrimebureau.net and hughestechgroup.com share the same IP address (69.28.69.4), indicating they are hosted on the same server:
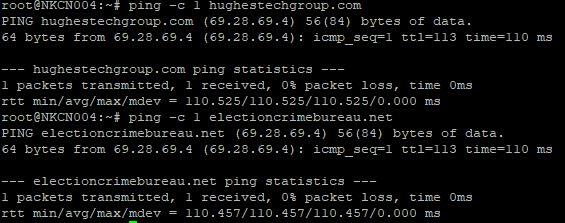
(Source: screenshot of the results of running the "ping" command on August 24, 2023 by Lead Stories)
Cybersecurity expert Robert Graham has written a good explanation about the many issues with this plan, concluding:
What's really going to happen is that Lindell volunteers will detect WiFi devices near polling places and go crazy. All poling places will have WiFi nearby. They'll demand that everything not otherwise explainable is evidence of their theory, that it's election machines that are connected to the Internet.
We must instead demand that they provide evidence. They must provide evidence these really are election machines, because it's impossible to prove they aren't. They must provide evidence they really are connected to the Internet. It's not our job to prove that these aren't the case, because we already know they'll find thousands of devices that false-positives.
Hughes Technology Group
Graham also found this URL on the Hughes Technology Group website (archived here) that appears to show more photos and videos of the device and the associated software. One of those videos (archived here) shows an impressive screen full of data and maps, quite similar to earlier Dennis Montgomery products. It appears to show a "Wireless Monitoring Device Command Center":
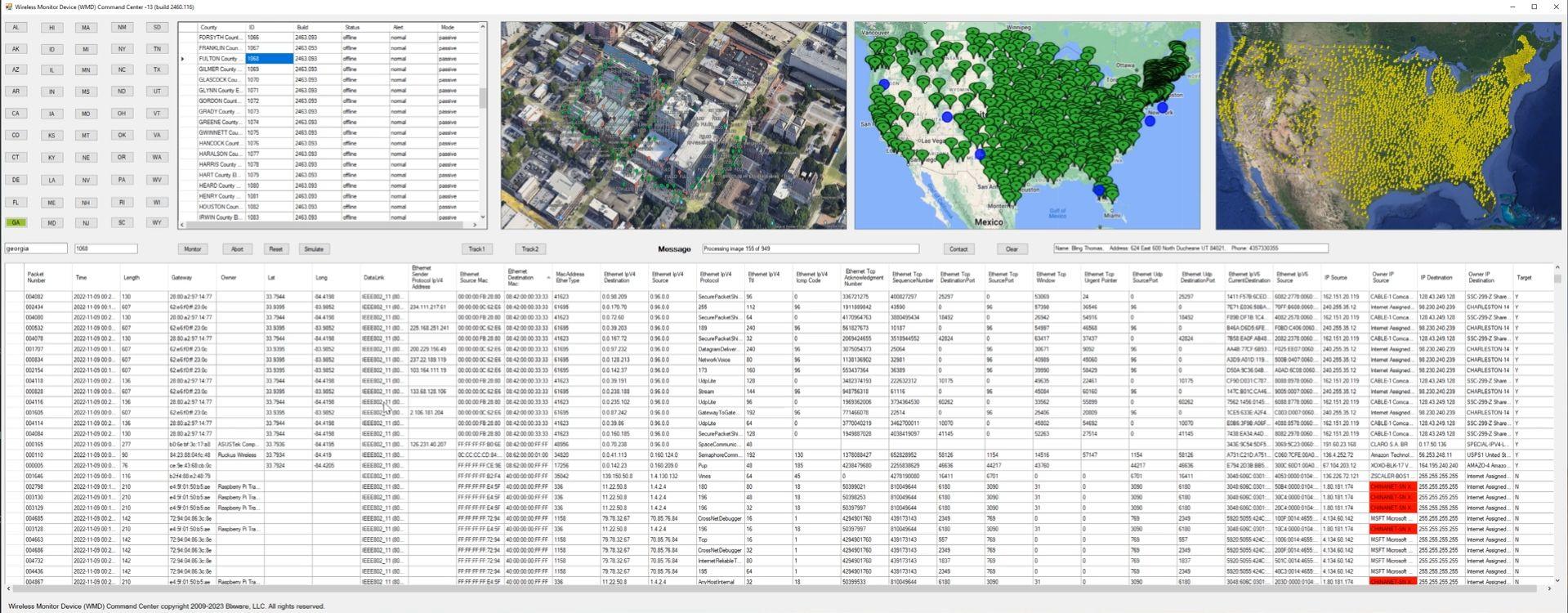
(Source: Screenshot of http://video21.org/video1/2023-06-23-15-48-16-Wmd-5-1.mp4?loop=1&autoplay=1 taken by Lead Stories on August 24,2023)
Larry Wright spotted that this video bears a Blxware copyright at the bottom, which is Dennis Montgomery's company:
(Source: Screenshot of http://video21.org/video1/2023-06-23-15-48-16-Wmd-5-1.mp4?loop=1&autoplay=1 taken by Lead Stories on August 24,2023)
Indeed, the main page of the Hughes Technology Group website (archived here) appears to be relatively new: according to the Internet Archive it was still showing a default webserver page on August 18, 2023. But currently it appears to be mostly a copy of the website of Blxware (archived here). The images even still link to blxware.com URLs.
(Source: Screenshots of hughestechgroup.com and blxware.com taken by Lead Stories on August 24, 2023)
But there is more information on http://hughestechgroup.com/site/wmd/index.html, the URL Robert Graham identified. One of the images showing off the WMD app shows an example email with the domain "wmd1.org" in a registration screen:

(Source: Screenshot of http://hughestechgroup.com/site/wmd/index.html taken by Lead Stories on August 24, 2023)
The website at https://wmd1.org (archived here) appears to be identical to the page at http://hughestechgroup.com/site/wmd/index.html, except for the copyright footer, which lists Blxware.com.
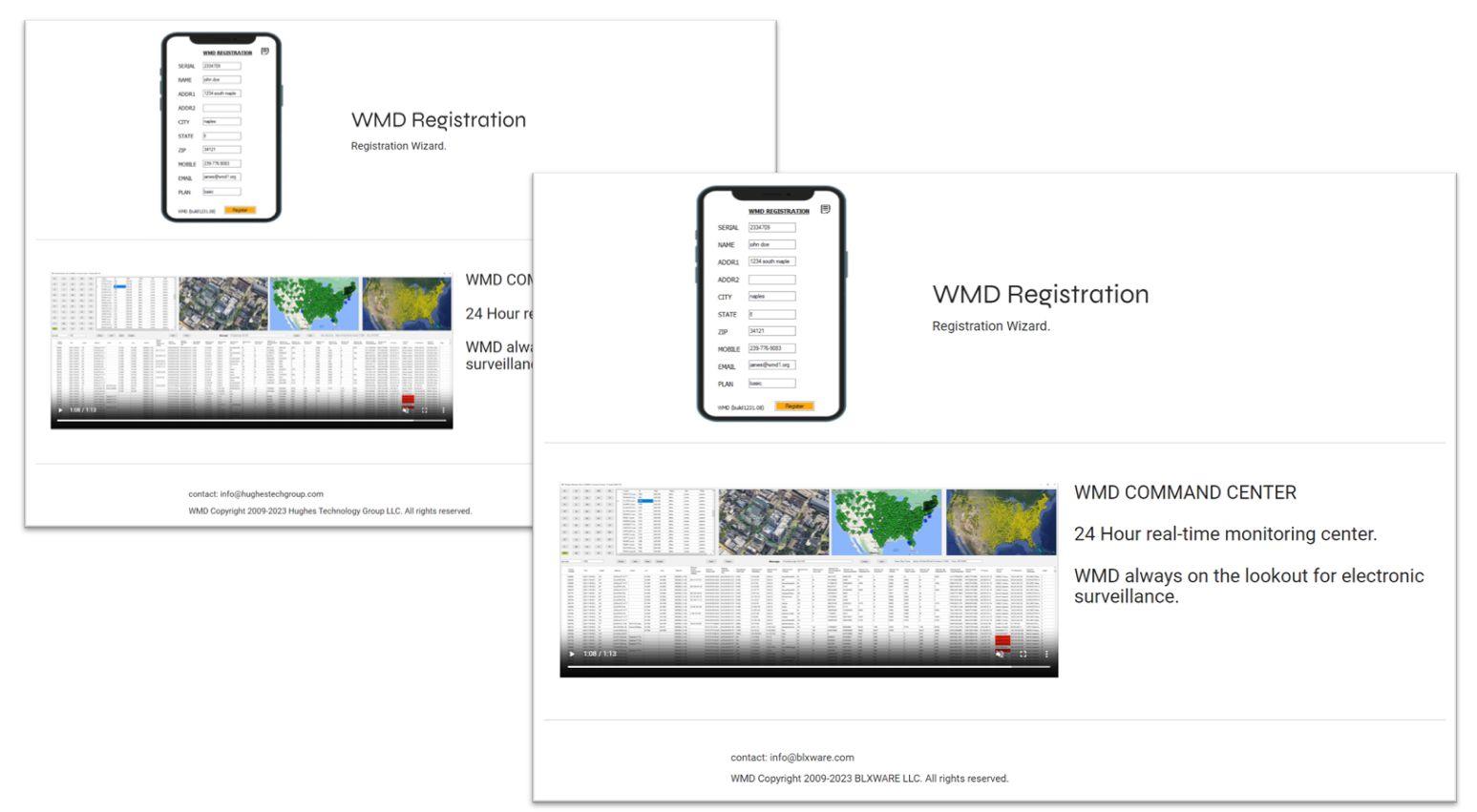
(Source: Screenshots of hughestechgroup.com and wmd1.org taken by Lead Stories on August 24, 2023)
It almost looks like there's a concerted effort here to hide links to Dennis Montgomery and Blxware. So we sent Mike Lindell an email on August 23, 2023, asking if Dennis Montgomery was involved with this project. Here is the reply that we received:
Dennis Montgomery just had back to back depositions and we turned over all the terabytes to the other sides and PCAPS
This is no explicit denial or confirmation of involvement in this project, but given all the above it would seem highly unlikely he wasn't involved. We sent Mike another email a day before publication of this article to ask for clarification but did not receive a reply yet.
Wigle room
In the first email we also asked Mike Lindell if he was aware of wigle.net, a website that has been logging wireless networks since 2001 and already has a billion of them on record in its database, and why he was choosing to build a new tool instead of relying on this existing project. Lindell's only comment on this was:
The device is not a Wi-Fi access point scanner.
In the Robert Graham article mentioned earlier, Graham speculated how the WMD device could work:
Once that problem is solve, then there are a ton of software packages to do the monitoring. They just receive and process packets. This WMD is probably just using Kismet and extensions for WIGLE. These are how most people do such WiFi monitoring these days. It would be silly not to.
Indeed, the second video on the website lindelloffensefund.com (archived here) shows a drone landing on stage at Lindell's Election Crime Bureau symposium just before Lindell and Jeff O'Donnell play a video to explain the WMD system. At the 2:27 timestamp a window briefly appears over the video, screenshotted below:
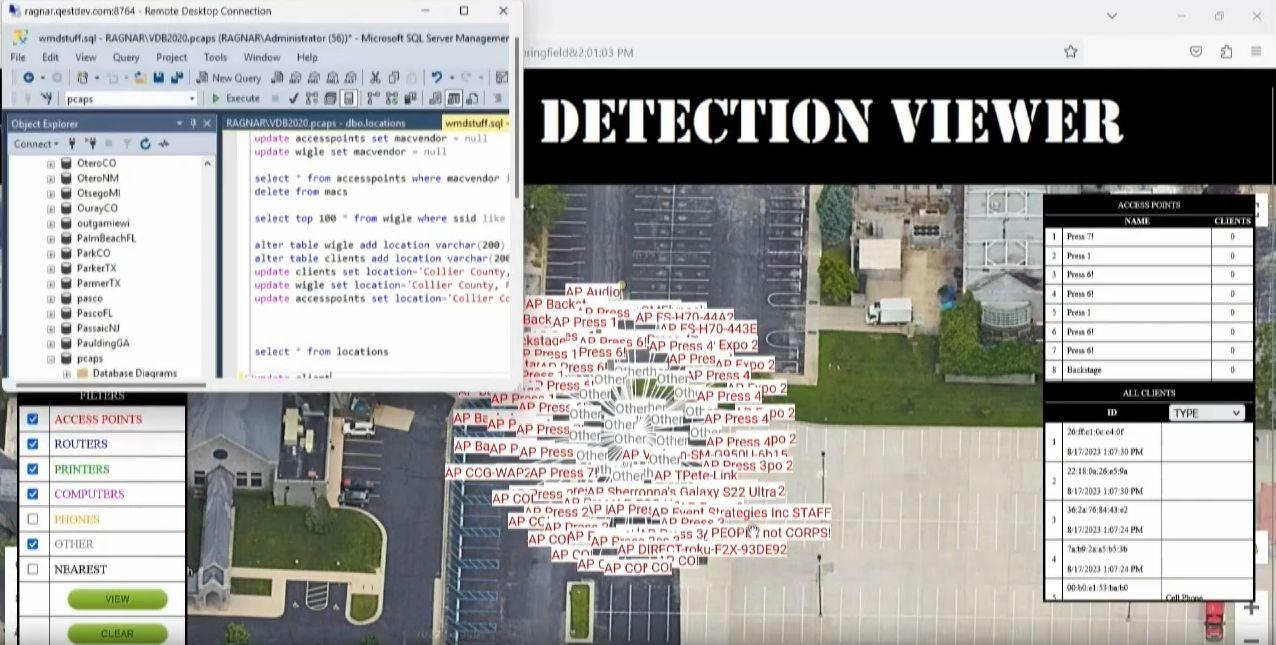
(Source: Screenshot of https://cdn.frankspeech.com/8f6b23b0-5be2-46df-b01a-d6cf75f07879/mp4/8f6b23b0-5be2-46df-b01a-d6cf75f07879.mp4 taken by Lead Stories on August 24,2023)
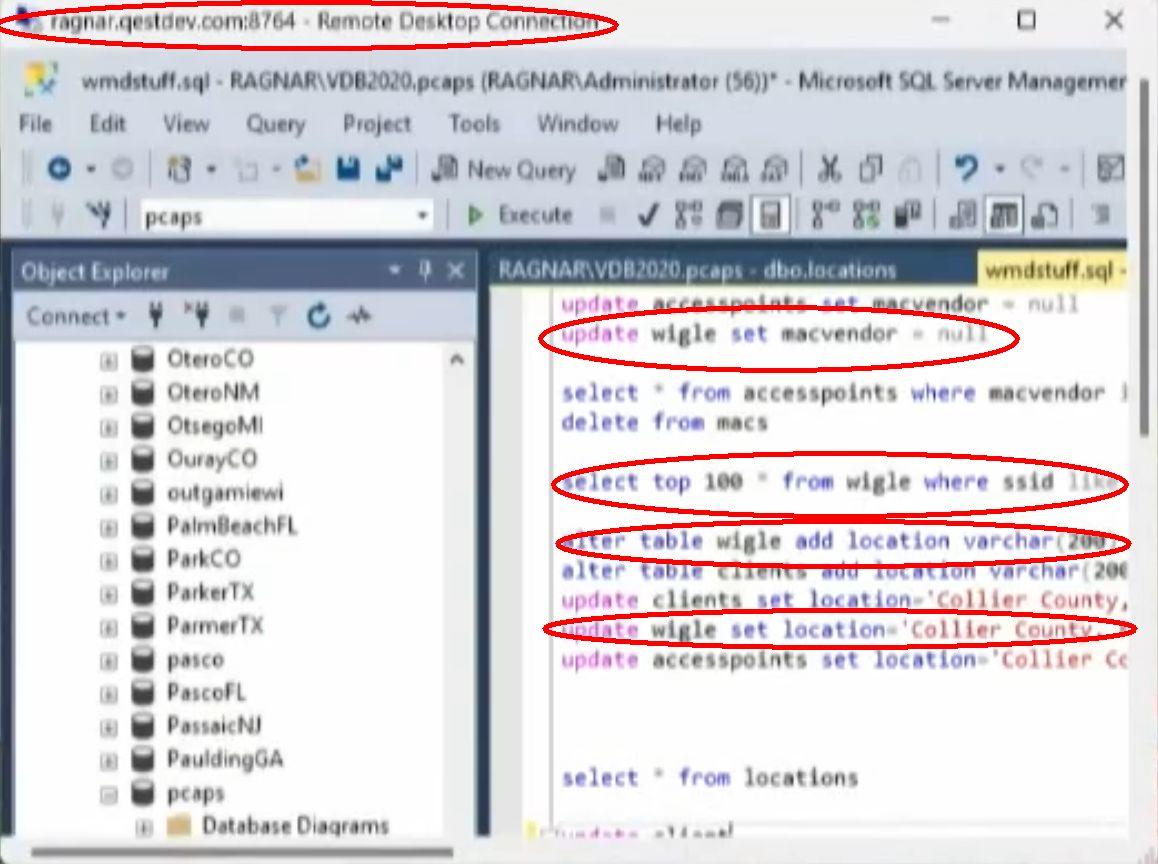
(Source: Screenshot of https://cdn.frankspeech.com/8f6b23b0-5be2-46df-b01a-d6cf75f07879/mp4/8f6b23b0-5be2-46df-b01a-d6cf75f07879.mp4 taken by Lead Stories on August 24,2023)
It appears to show a remote desktop connection to a server named ragnar.qestdev.com, showing an open application named "Microsoft SQL Server Management" with a list of several database queries relating to "wigle" in a file named "wmdstuff.sql."
Qestdev (archived here) appears to be the company of Jeff O'Donnell, and the IP of ragnar.qestdev.net is 69.28.69.3, just one digit away from 69.28.69.4, the IP of electioncrimebureau.net and hughestechgroup.com. It looks like it was O'Donnell doing the demo when the window with the wigle SQL queries briefly appeared on screen by accident.
It is unclear if these queries are for using data obtained from Wigle or if they are meant to store data in a format that can be used by Wigle. Or perhaps it was all just a coincidence?
We asked Jeff O'Donnell for comment by email a day before publishing this article, using the email address listed on his website. We haven't received a reply so far. We did the same for Dennis Montgomery.
What does this all mean?
Is Mike Lindell really launching a nationwide effort to scan for Wi-Fi and other signals near polling stations using sophisticated technology? Or did Dennis Montgomery build him another impressive-looking website that will use possibly falsified and/or publicly available data to create a dazzling spectacle that has no actual evidentiary value? It is too early to tell, since none of the data collected by the project has been made public yet. But we'll be watching with great interest.
Note that the demo video on the Hughes Technology Group website shows data from 2022 and already conveniently highlights China-related entries. It also has maps with pins on them covering pretty much the entire United States already. All the dates on the data entries are identical too so it would seem all of it was supposedly collected in a single day. This despite the fact that the WMD project was only launched by Mike Lindell in August 2023 so it would seem to be impossible for this nationwide data to have been collected by volunteers using the WMD (unless there is a time machine involved of course).
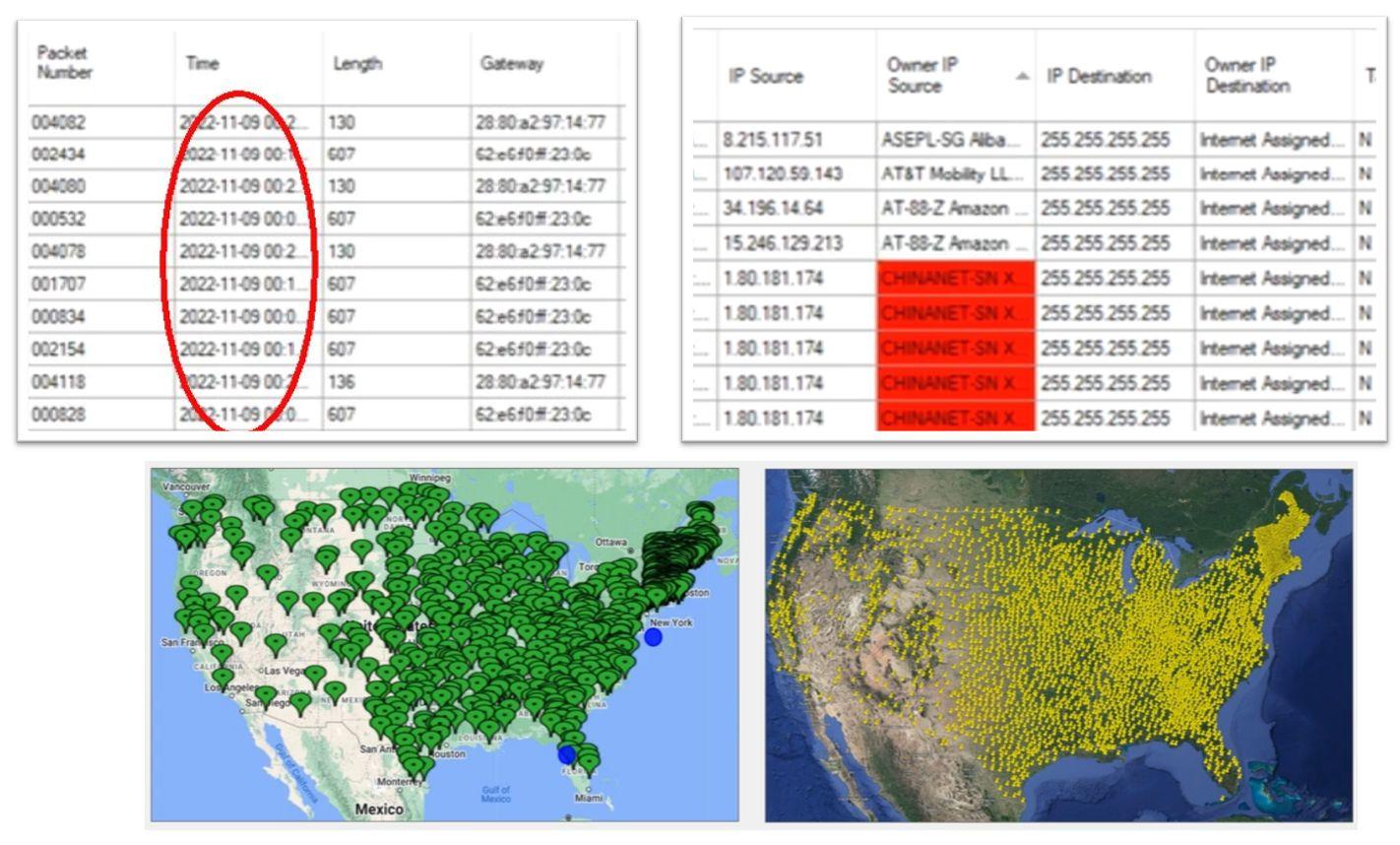
(Source: Collage based on screenshot of http://video21.org/video1/2023-06-23-15-48-16-Wmd-5-1.mp4?loop=1&autoplay=1 taken by Lead Stories on August 24,2023)
The distribution of the yellow dots on the map also looks similar to the distribution of the Wi-Fi hotspots on wigle.net (which nicely shows there are more Wi-Fi signals where more people live):
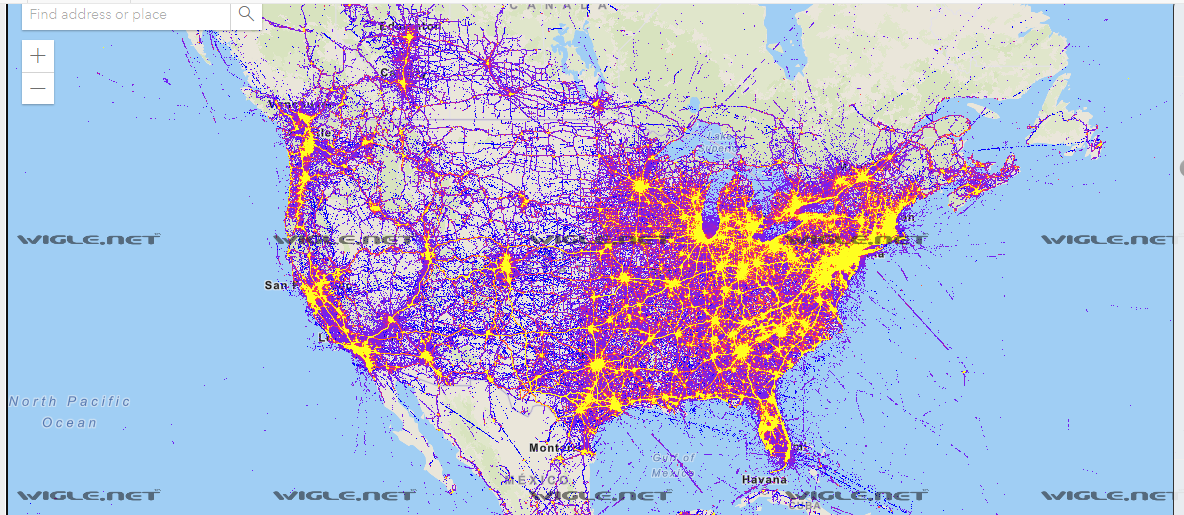
(Source: Screenshot from wigle.net taken August 23, 2023 by Lead Stories)
So, was the demo just using sample data from Wigle? Could be. But it seems odd that a brand new Wi-Fi scanning tool with websites that according to WHOIS data were registered only in June and July of 2023 would show 2022 data in its demo video.
Is someone making things up to fool someone? And who is fooling who here? We don't know yet. But if this tool ever gets used during an election we will be closely comparing its output with public Wigle data, that's for sure.
Cryptic message
One last observation: The first capture the Internet Archive made of the WMD tool on Dennis Montgomery's Hugues Technology Group website shows a cryptic message:
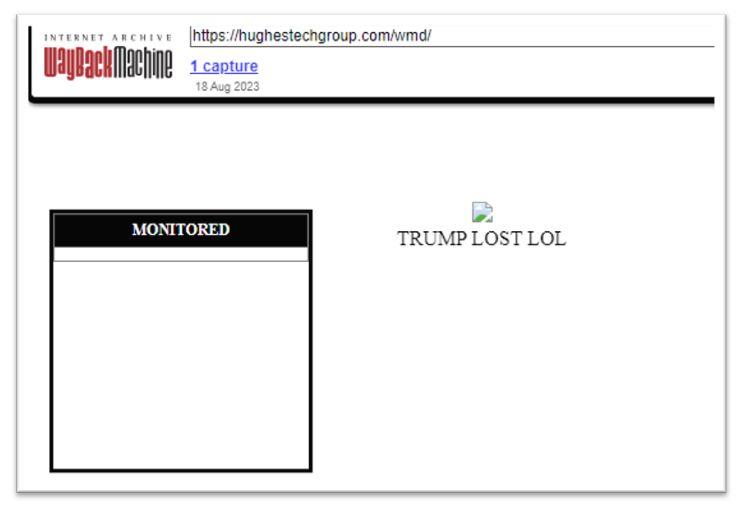
(Source: Screenshot of https://web.archive.org/web/20230818112155/https://hughestechgroup.com/wmd/ made on August 24, 2023 by Lead Stories)
Subtle dig at the people who believe the tool is real? Subtle dig at the people paying for the tool?
Who can say?